AES vs DES: Which Encryption Algorithm is More Secure in 2025?
Data Encryption Standard (DES) was once the gold standard for symmetric encryption, but its limitations have become apparent over time. Advanced Encryption Standard (AES), on the other hand, represents modern cryptographic excellence. Understanding the des vs aes comparison is crucial for making informed security decisions in today’s digital landscape.
Understanding DES Encryption
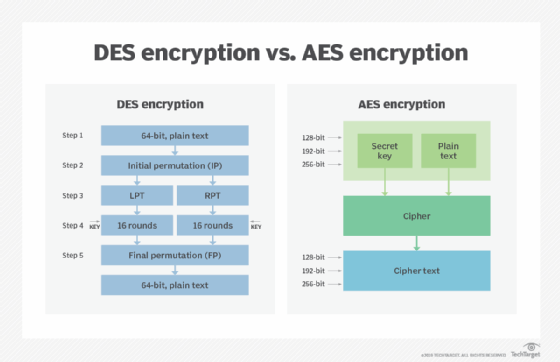
DES emerged in the 1970s as a federal standard for protecting sensitive government communications. This symmetric block cipher uses a 56-bit key length and processes data in 64-bit blocks. The algorithm employs a Feistel network structure with 16 rounds of encryption, making it revolutionary for its time.
The encryption process involves initial permutation, followed by 16 rounds of complex operations including expansion, substitution, and permutation. Each round uses a different subkey derived from the main 56-bit key through a key schedule algorithm.
Despite its historical significance, DES faces serious security vulnerabilities. The relatively small key space of 2^56 possible keys makes it susceptible to brute-force attacks using modern computing power. Additionally, differential and linear cryptanalysis techniques have revealed weaknesses in the algorithm’s structure.
The Evolution to Triple DES
Recognizing DES’s limitations, cryptographers developed Triple DES (3DES) as an interim solution. The triple des vs aes comparison reveals interesting insights about transitional cryptographic approaches.
Triple DES applies the DES algorithm three times to each data block, effectively extending the key length to 112 or 168 bits depending on the implementation. The most common variant uses two keys (2TDES) with an encrypt-decrypt-encrypt sequence, while the more secure version uses three independent keys (3TDES).
This approach significantly improves security compared to standard DES by exponentially increasing the computational effort required for brute-force attacks. However, Triple DES inherits some of DES’s structural weaknesses and operates considerably slower than modern alternatives.
The algorithm’s backward compatibility with existing DES infrastructure made it attractive for organizations during the transition period. Financial institutions, in particular, relied heavily on Triple DES for payment processing and secure communications.
Introduction to AES Encryption
AES represents a paradigm shift in symmetric encryption technology. Developed through an open competition organized by the National Institute of Standards and Technology (NIST), AES was selected from multiple candidate algorithms based on security, performance, and implementation flexibility.
The algorithm, originally known as Rijndael, supports three key lengths: 128, 192, and 256 bits. Unlike DES’s Feistel structure, AES uses a substitution-permutation network that processes data through multiple rounds of transformation.
AES-128 performs 10 rounds, AES-192 uses 12 rounds, and AES-256 employs 14 rounds. Each round consists of four operations: SubBytes (substitution), ShiftRows (transposition), MixColumns (mixing), and AddRoundKey (key addition).
The algorithm’s design philosophy emphasizes resistance against all known cryptanalytic attacks while maintaining efficient implementation across various platforms. Its mathematical foundation in finite field arithmetic provides strong theoretical security guarantees.
Security Analysis: Key Length and Cryptographic Strength
The aes vs triple des security comparison reveals substantial differences in cryptographic strength. Key length serves as a primary indicator of encryption robustness, but it’s not the only factor determining security.
DES’s 56-bit key provides only 2^56 possible combinations, which modern computers can exhaust in reasonable time frames. Specialized hardware can break DES encryption in hours or days, making it unsuitable for protecting sensitive information.
Triple DES with two keys offers approximately 80 bits of security strength, while three-key Triple DES provides about 112 bits. Although significantly better than standard DES, these levels fall short of current security recommendations.
AES dramatically improves upon these figures. AES-128 provides 128 bits of security strength, AES-192 offers 192 bits, and AES-256 delivers 256 bits. Even the smallest AES variant provides security levels that would require astronomical computational resources to break using current technology.
The time complexity for brute-force attacks illustrates these differences clearly. Breaking AES-128 would require approximately 2^128 operations, a number so large that it exceeds the estimated number of atoms in the observable universe.
Performance and Efficiency Considerations
Modern encryption systems must balance security with operational efficiency. Performance characteristics significantly impact user experience and system resource utilization.
DES, despite its security limitations, operates relatively quickly due to its simple structure and modest computational requirements. However, its performance advantage becomes meaningless when security is compromised.
Triple DES suffers from significant performance penalties because it applies the DES algorithm three times to each data block. This approach roughly triples the processing time compared to standard DES, making it inefficient for high-throughput applications.
AES excels in both security and performance metrics. Modern processors include specialized instruction sets (AES-NI) that accelerate AES operations, enabling encryption and decryption speeds that often exceed Triple DES despite providing superior security.
Benchmark studies consistently demonstrate AES’s efficiency advantages. On typical hardware, AES-128 performs significantly faster than Triple DES while providing substantially better security. This performance superiority extends across various implementation scenarios, from embedded systems to high-performance servers.
Implementation and Hardware Support
Practical deployment considerations play crucial roles in encryption algorithm selection. Hardware support, software libraries, and integration complexity all influence implementation decisions.
DES enjoys widespread legacy support across numerous platforms and devices. However, this compatibility comes at the cost of security, making it unsuitable for new implementations.
Triple DES maintains compatibility with existing DES infrastructure while providing improved security. Many payment processing systems and legacy applications continue using Triple DES due to established certification processes and regulatory requirements.
AES benefits from extensive modern hardware acceleration and optimized software implementations. Most contemporary processors include dedicated AES instruction sets that dramatically improve performance while reducing power consumption.
The algorithm’s flexible design supports various implementation approaches, from lightweight embedded systems to high-performance cryptographic accelerators. This versatility makes AES suitable for diverse application scenarios.
Industry Standards and Compliance Requirements
Regulatory frameworks and industry standards significantly influence encryption algorithm adoption. Understanding compliance requirements helps organizations make appropriate security decisions.
Federal Information Processing Standards (FIPS) 140-2 and Common Criteria evaluations provide formal security certifications for cryptographic implementations. AES holds the highest security ratings under these frameworks, while DES is no longer approved for new applications.
Payment Card Industry (PCI) standards mandate strong encryption for protecting cardholder data. Current PCI requirements prohibit DES usage and are phasing out Triple DES in favor of AES.
International standards organizations, including ISO/IEC and NIST, consistently recommend AES for new cryptographic implementations. These recommendations reflect extensive security analysis and industry consensus regarding algorithm strength.
Future-Proofing and Quantum Resistance
Emerging threats, particularly quantum computing, require forward-thinking security strategies. Understanding long-term viability helps organizations prepare for future challenges.
Quantum computers pose theoretical threats to current encryption algorithms through algorithms like Grover’s search, which effectively halves the security strength of symmetric ciphers. AES-256 would provide approximately 128 bits of post-quantum security, while smaller key sizes might require replacement.
DES and Triple DES offer inadequate protection against quantum threats due to their already limited key spaces. Organizations relying on these algorithms face immediate vulnerability concerns without considering quantum computing advances.
Post-quantum cryptography research continues developing quantum-resistant algorithms, but AES remains the recommended choice for symmetric encryption in transitional periods. Its larger key sizes provide better quantum resistance compared to older alternatives.
Best Practices and Recommendations
Selecting appropriate encryption algorithms requires careful consideration of security requirements, performance constraints, and compliance obligations.
For new implementations, AES represents the clear choice due to its superior security, excellent performance, and broad industry support. Organizations should prefer AES-256 for high-security applications and AES-128 for general-purpose encryption needs.
Legacy systems using DES require immediate migration planning due to fundamental security weaknesses. The algorithm provides insufficient protection against modern attack methods and should not be used for sensitive data protection.
Triple DES serves as an acceptable interim solution for systems transitioning from DES, but organizations should prioritize migration to AES. Regulatory changes and performance limitations make Triple DES unsuitable for long-term deployment.
Proper key management, secure implementation practices, and regular security assessments remain essential regardless of algorithm choice. Even the strongest encryption algorithms become vulnerable when implemented incorrectly or managed poorly.
Regular security audits, penetration testing, and compliance assessments help ensure continued protection effectiveness. Organizations should also monitor emerging threats and cryptographic research to anticipate future security requirements.
The cryptographic landscape continues evolving, but AES currently represents the gold standard for symmetric encryption. Its combination of security, performance, and industry support makes it the optimal choice for protecting sensitive information in 2025 and beyond.