Advanced encryption standard AES is the cornerstone of modern digital security. As businesses, governments, and individuals rely more on digital systems, ensuring data safety has become essential. This guide explores what advanced encryption standard AES is, how it works, its applications, benefits, and real-world examples. We answer critical questions such as “what is advanced encryption standard” and compare AES to other cryptographic systems to help you make informed decisions about securing your data. For readers new to cryptography, you may find our comprehensive beginner guide to symmetric encryption helpful.
What Is Advanced Encryption Standard AES?
Advanced encryption standard AES is a symmetric key block cipher, meaning it divides data into blocks before encrypting and uses the same key for both encryption and decryption. Advanced encryption standard was established as a federal standard by the U.S. National Institute of Standards and Technology (NIST) in 2001, AES replaced the outdated Data Encryption Standard (DES). Designed for efficiency, security, and flexibility, AES is widely used across industries to secure everything from online banking to classified government communications.
Key Attributes of AES
- Symmetric Encryption:
Advanced encryption standard is a symmetric encryption algorithm, meaning it uses the same secret key for both encrypting and decrypting the data. This makes it faster and simpler than asymmetric methods, but it also means that securely sharing and managing the key is very important to prevent unauthorized access. - Block Cipher:
Advanced encryption standard works as a block cipher, which means it divides data into fixed chunks, or blocks, of 128 bits each. Every block is processed in the same secure way, ensuring that large amounts of data maintain a consistent level of protection. This structured approach makes AES both reliable and predictable in how it safeguards information. - Variable Key Lengths:
One of the strengths of AES is its flexibility in key size. It allows the use of 128, 192, or 256-bit keys. A longer key length provides stronger security against brute-force attacks, while shorter keys offer faster performance. This gives users the choice to select the right balance depending on their security needs and system capabilities. - Fast and Resource-Efficient:
AES is designed to be highly efficient on both software and hardware platforms. It can handle large volumes of data quickly without consuming too many system resources. This efficiency makes it practical for a wide range of applications, from encrypting files on personal devices to securing large-scale communications in businesses and governments.
Keying Options in AES
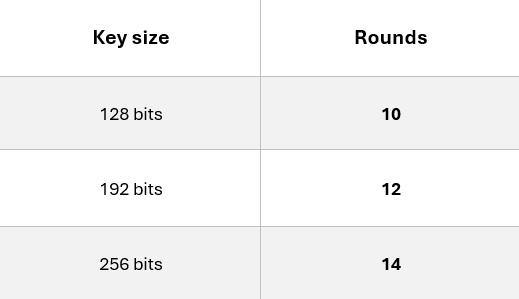
Advanced encryption standard offers three key size options, which determine how secure the encryption is and how many rounds of transformation are applied during the process. The larger the key, the stronger the protection, but it may require slightly more computing power.
- 128-bit Key:
This is the most common version of AES. It uses 10 rounds of encryption and provides strong security while being very fast. It’s widely used in applications like Wi-Fi security, file encryption, and secure web connections. - 192-bit Key:
With 12 rounds of encryption, the 192-bit key version offers a higher level of security. It’s less common than 128-bit but is often chosen in industries or systems where extra protection is needed without too much impact on performance. - 256-bit Key:
This is the strongest option, using 14 rounds of encryption. It’s highly resistant to brute-force attacks, making it suitable for protecting extremely sensitive data such as government, financial, or defense communications. While it requires more processing power, modern systems can handle it efficiently.
How Does the Advanced Encryption Standard Work?
Advanced encryption standard AES works by transforming readable information (plaintext) into scrambled code (ciphertext) through a series of well-defined steps. It relies on a secret key and mathematical operations to ensure that only someone with the correct key can reverse the process and recover the original data.
-
Input as Blocks:
The data is first divided into fixed-size blocks of 128 bits. Each block is processed independently, which ensures consistency and security across the entire message. -
Rounds of Transformation:
Depending on the key size (128, 192, or 256 bits), AES applies 10, 12, or 14 rounds of encryption steps. Each round uses substitution, permutation, and mixing operations that shuffle and alter the data, making it extremely difficult to guess or reverse without the key. -
Use of the Secret Key:
The secret key is expanded into multiple “round keys,” which are applied at every step of the encryption process. These round keys ensure that even small changes in the key completely change the output, adding strength against attacks. -
Decryption Process:
To decrypt, AES simply runs the process in reverse using the same key. This way, the ciphertext is transformed back into its original readable form (plaintext).
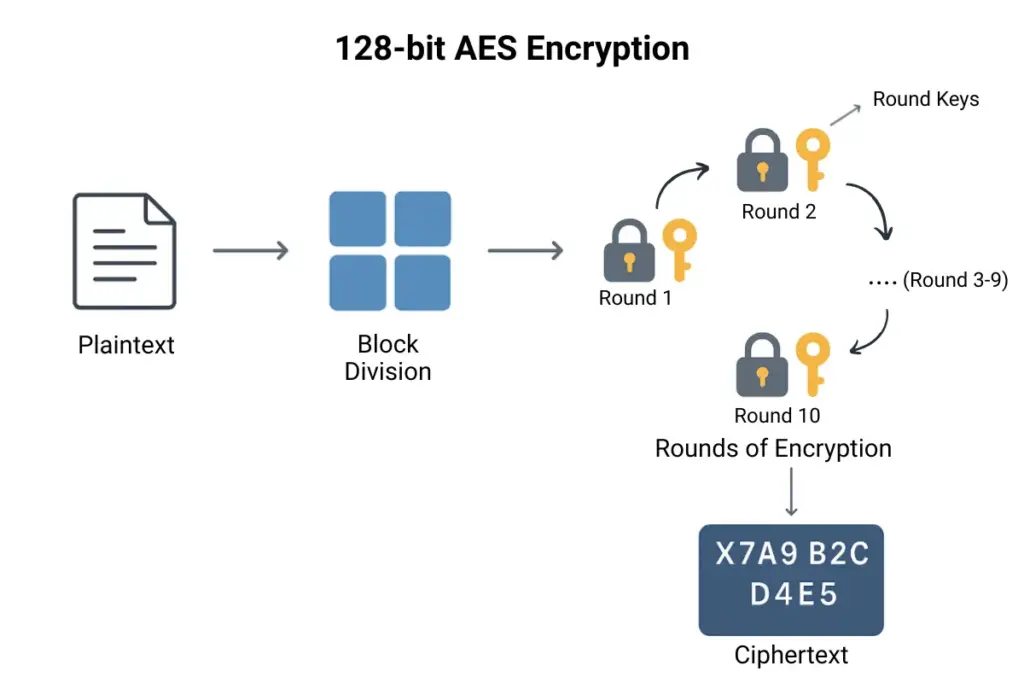
In short, Advanced encryption standard AES works by repeatedly applying layers of mathematical transformations to data blocks, with the secret key guiding the process. This combination of structure, repetition, and key dependence makes AES both highly secure and efficient.
Structure of Each Round in AES
Advanced encryption standard AES is built on a substitution–permutation network, which means it relies on a series of structured mathematical steps to scramble and secure data. These steps are applied in multiple rounds, guided by the secret key, to ensure that the output is unpredictable and resistant to attacks.
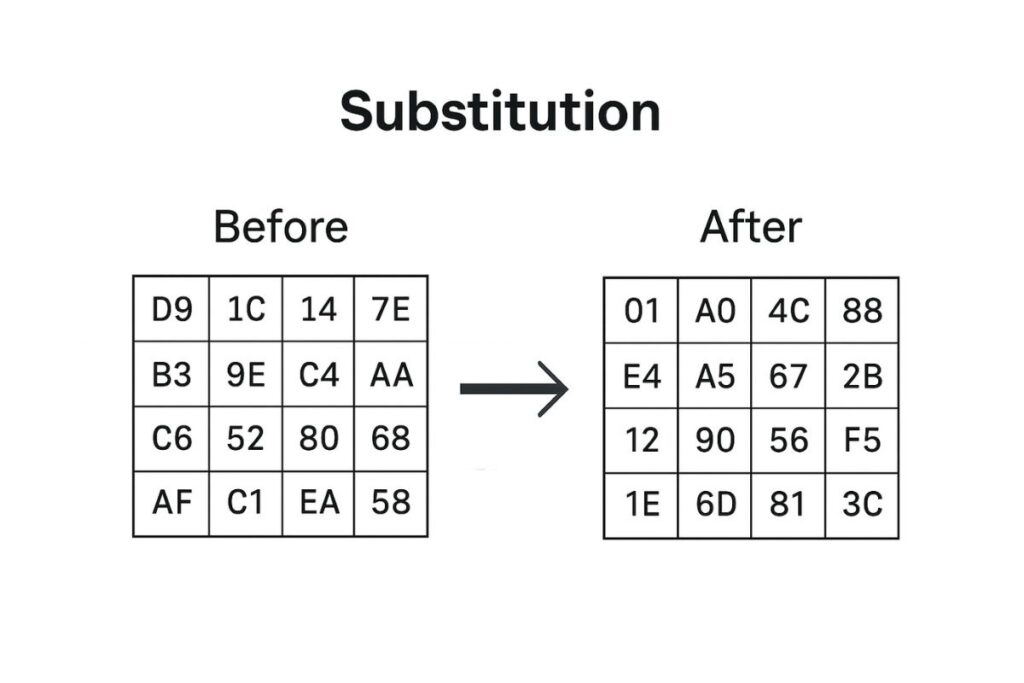
Substitution (SubBytes)
Each byte of data is replaced with another using a substitution table (S-box), introducing confusion in the data.
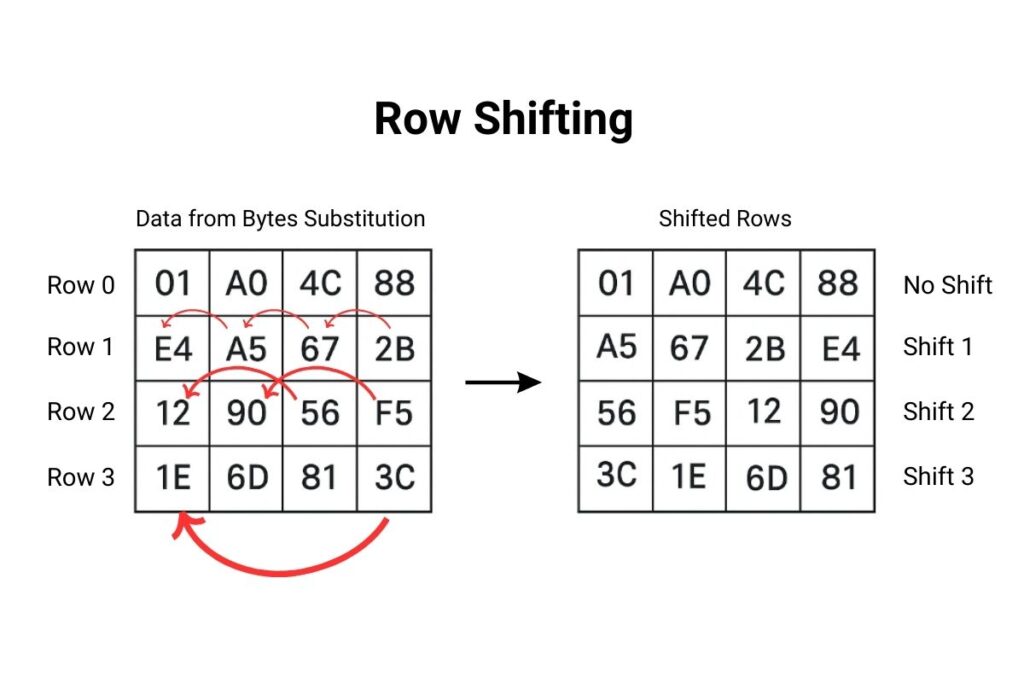
Row Shifting (ShiftRows)
Rows of the block are shifted to the left by different offsets, rearranging the data and increasing complexity.
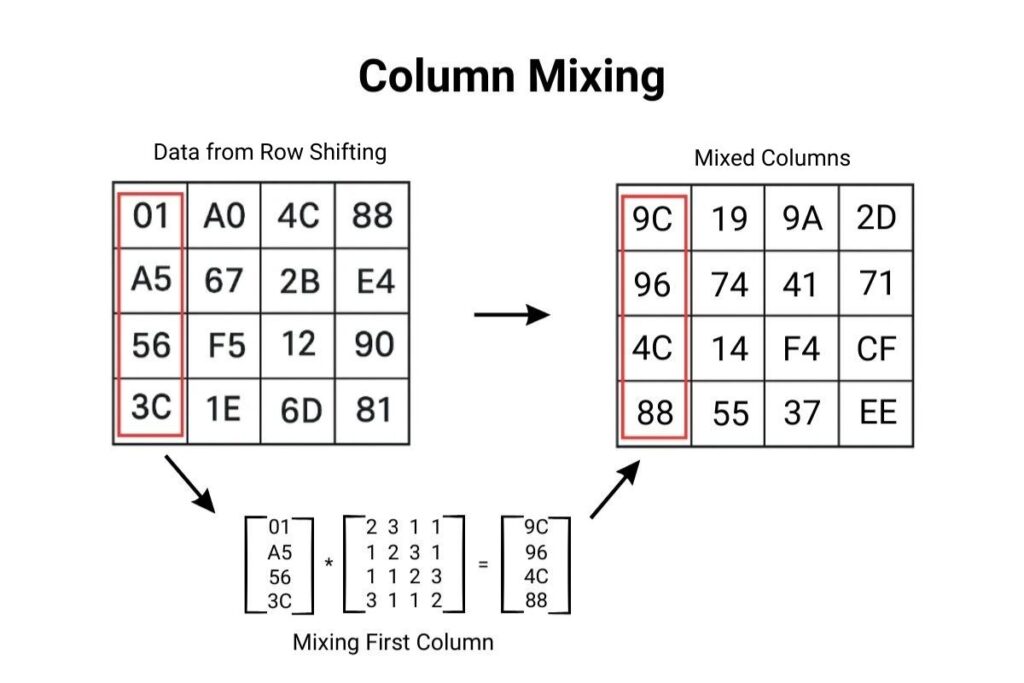
Column Mixing (MixColumns)
Data within columns is mixed using mathematical operations, further disguising patterns.
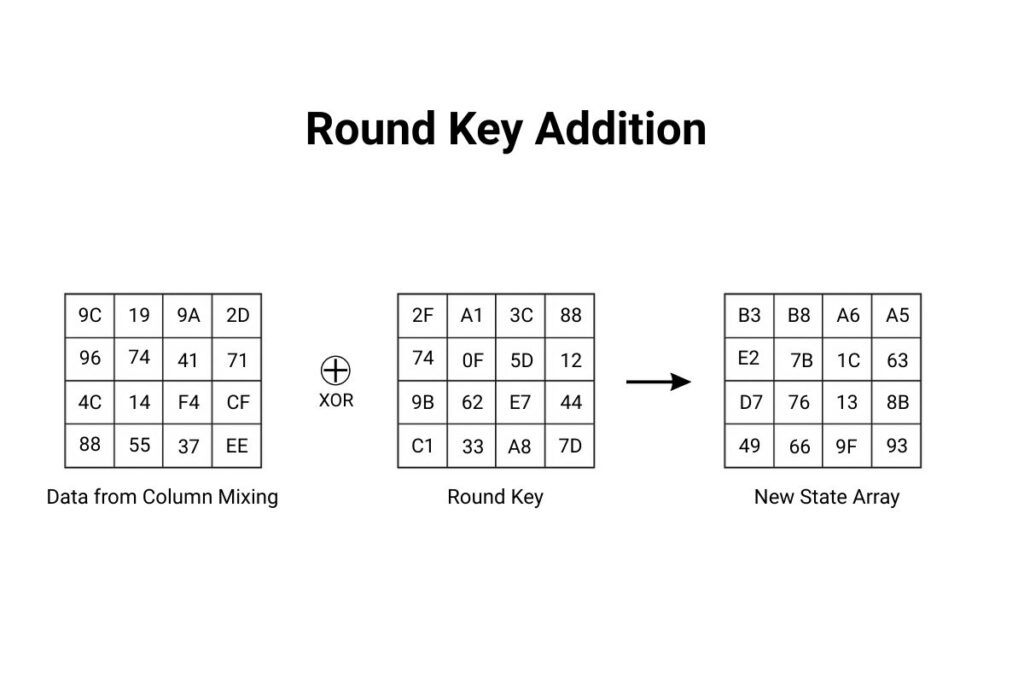
Round Key Addition (AddRoundKey)
At every round, the block is combined with a round-specific key, ensuring the key plays a role in every transformation.
These steps are performed repeatedly until all rounds are completed. The final round omits the MixColumns step to ensure reversibility during decryption. This structured sequence makes AES both secure and efficient, and because it’s designed for reversibility, the same steps can be undone during decryption when the correct key is provided.
Modes of Operation in AES
Advanced Encryption Standard AES on its own is a block cipher — it encrypts fixed-size 128-bit blocks. To securely encrypt larger messages, different modes of operation are used. Each mode defines how blocks are processed and linked together during encryption and decryption.
1. Electronic Codebook (ECB)
-
Simplest mode: each block is encrypted independently with the same key.
-
Pros: Fast, easy to implement.
-
Cons: Identical plaintext blocks → identical ciphertext blocks (pattern leakage).
-
Use Case: Rarely recommended; mostly for test/debugging.
2. Cipher Block Chaining (CBC)
-
Each plaintext block is XORed with the previous ciphertext block before encryption.
-
Requires an Initialization Vector (IV) for the first block.
-
Pros: Hides plaintext patterns.
-
Cons: Slower, and one wrong block can mess up the next one.
-
Use Case: Secure file encryption, database fields.
3. Cipher Feedback (CFB)
-
Converts block cipher into a self-synchronizing stream cipher.
-
Previous ciphertext is encrypted and XORed with the current plaintext.
-
Pros: Can work on data smaller than a block; stream-like operation.
-
Cons: If there’s an error, it affects more than one block.
-
Use Case: Real-time data streams (e.g., communication channels).
4. Output Feedback (OFB)
-
Similar to CFB, but keystream is generated independent of plaintext/ciphertext.
-
Pros: Errors do not propagate; precomputation possible.
-
Cons: Reuse of IV is dangerous (same keystream repeats).
-
Use Case: Secure streaming, error-sensitive environments.
5. Counter Mode (CTR)
-
Uses a counter value encrypted with the key to generate a keystream.
-
Counter increments for each block.
-
Pros: Fully parallelizable, random access to encrypted data.
-
Cons: If the counter is ever reused, security breaks.
-
Use Case: High-performance network encryption, disk encryption.
Why use Advanced Encryption Standard
Security professionals universally trust advanced encryption standard AES due to its robustness and resistance to known attacks. The algorithm has undergone rigorous scrutiny and is widely adopted.
Benefits:
-
Trusted Worldwide: AES is approved by security experts and governments across the globe, including the U.S. National Institute of Standards and Technology (NIST).
-
Strong Security: With support for long key sizes (128, 192, and 256 bits), AES is extremely hard to break, even with powerful computers.
-
Fast and Efficient: It protects data quickly without slowing down devices, making it ideal for both personal gadgets and large servers.
-
Everywhere in Use: From securing Wi-Fi and mobile apps to protecting classified government information, AES is at the heart of modern cybersecurity.
In short, AES matters because it combines strong protection, speed, and wide adoption, making it the standard choice for keeping sensitive information secure.
Advanced Encryption Standard AES Example
To understand AES better, let’s walk through a very basic example of how it works:
Plaintext (original message):
HELLO123
Convert to blocks:
Advanced encryption standard AES works on fixed blocks of 16 bytes. The message is converted into numbers/hex values to fill the block.
Key (secret password):
For example, a 128-bit key (16 characters like MYSECRETKEY12345).
Encryption Process (simplified):
- The message block is combined with the key.
- Several rounds of substitution, shifting, mixing, and adding the key are performed.
- Each round scrambles the data more, making it unreadable without the correct key.
Ciphertext (encrypted message):
The output looks like random characters, e.g.:
9C 19 9A 2D 96 74 41 71 …
Decryption:
Using the same key, AES runs the steps in reverse to get back the original message.
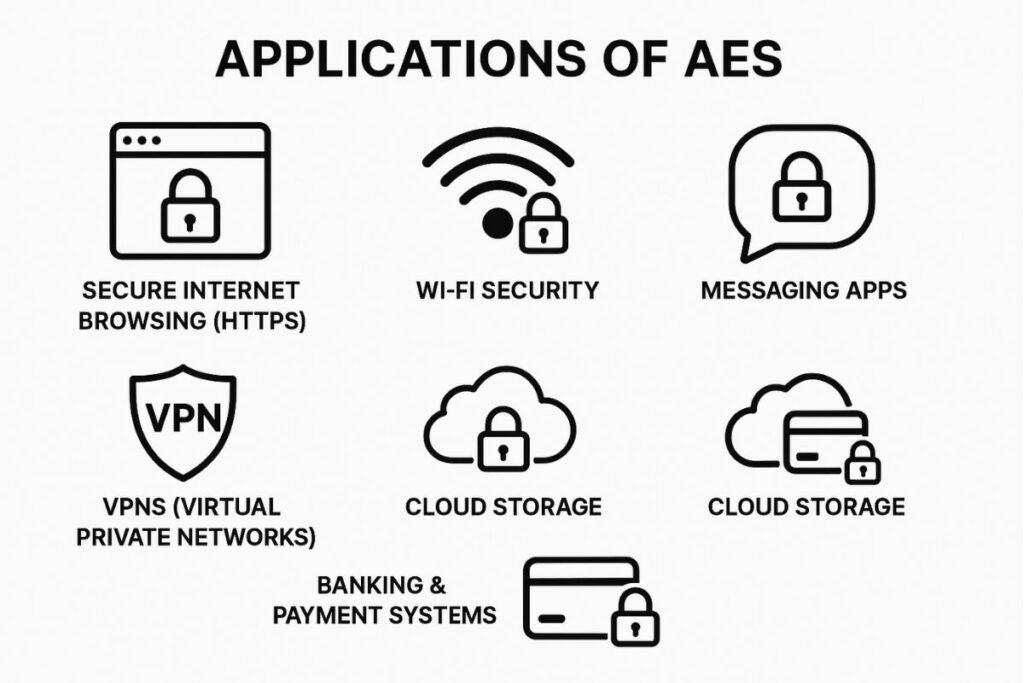
Applications of AES
The advanced encryption standard AES is used almost everywhere in the digital world to keep data safe. Some common applications are:
-
Secure Internet Browsing (HTTPS):
When you see a padlock in your browser, AES is working behind the scenes to encrypt your connection. -
Wi-Fi Security:
Advanced encryption standard AES is part of WPA2 and WPA3, the standards that protect your wireless networks from hackers. -
File and Disk Encryption:
Tools like BitLocker, VeraCrypt, and FileVault use AES to keep your files and drives safe from unauthorized access. -
Messaging Apps:
Popular apps like WhatsApp, Signal, and Telegram rely on AES to make sure your chats can only be read by the intended person. -
VPNs (Virtual Private Networks):
AES encrypts all your internet traffic when you use a VPN, preventing snooping from hackers or ISPs. -
Cloud Storage:
Services like Google Drive, Dropbox, and OneDrive use AES to secure the files you upload. -
Banking & Payment Systems:
Online banking and digital payment platforms rely on AES to protect sensitive financial transactions.
Evolution and Importance of the Advanced Encryption Standard
“What is advanced encryption standard?” can be answered by tracing its evolution. Advanced encryption standard AES was selected via a global competition, beating other proposals due to its efficiency, simplicity, and lack of known weaknesses.
Evolution of AES:
Before Advanced encryption standard AES, the Data Encryption Standard (DES) was widely used. Over time, DES became weak because of advances in computing power that could break it. In 1997, the U.S. National Institute of Standards and Technology (NIST) launched a global competition to find a stronger, more secure replacement. In 2001, Rijndael, designed by Joan Daemen and Vincent Rijmen, was selected and became the official AES standard. NIST’s adoption of the Rijndael algorithm, the basis of AES, resulted in a standard tough enough for national and commercial use. Today, Advanced encryption standard AES is the gold standard for both symmetric encryption algorithms and global data protection strategies.
Importance of AES:
-
Security: AES provides strong encryption that protects sensitive data worldwide.
-
Efficiency: It works fast in both hardware and software, making it practical for real-world use.
-
Trust: AES is used by governments, businesses, and individuals, proving its reliability.
-
Longevity: Even today, AES remains resistant to modern attacks and is considered future-ready.
AES Versus Other Encryption Methods
While advanced encryption standard AES is widely used, other symmetric and asymmetric algorithms exist. For a detailed side-by-side, check our AES vs DES comparison.
- DES: Once standard, now obsolete due to short key length (56 bits) and vulnerability to brute-force attacks. Learn more in our Data Encryption Standard guide.
- Triple DES: Improves DES by applying encryption three times, but is slower and less secure than AES. Explore detailed use cases in our Triple DES overview.
- RSA: Asymmetric algorithm for secure key exchange and digital signatures, but not suited to bulk data encryption due to performance limitations. See our RSA encryption deep dive and asymmetric key methods.
- Blowfish, Twofish, Serpent: Other symmetric algorithms with unique strengths. Compare Blowfish in our Blowfish encryption guide and Twofish in our Twofish tutorial.
AES balances speed, security, and accessibility, making it the preferred choice for most contemporary applications.
How to Implement AES Securely
Advanced encryption standard AES is one of the strongest encryption standards available, but using it incorrectly can make systems vulnerable. To ensure proper security, here are some best practices:
-
Always use a secure mode of operation – Avoid ECB (Electronic Codebook) mode since it can reveal patterns in data. Instead, use CBC, GCM, or CTR depending on your needs.
-
Generate strong keys – Keys should be truly random and of sufficient length (128, 192, or 256 bits).
-
Protect the key – Store encryption keys securely (e.g., using Hardware Security Modules or Key Management Systems). Never hardcode them into applications.
-
Use Initialization Vectors (IVs) correctly – IVs must be unique and unpredictable for each encryption session.
-
Authenticate your data – Combine AES with authentication (like AES-GCM or HMAC) to prevent tampering.
-
Regularly update keys – Key rotation helps limit the impact if a key is ever compromised.
-
Rely on trusted libraries – Instead of writing AES from scratch, use well-tested cryptographic libraries.
When implemented with these guidelines, AES provides reliable and future-proof protection for sensitive information.
Known Attacks and Security Concerns
No cipher is immune to poor implementation. Though advanced encryption standard AES is mathematically robust, common weaknesses often stem from weak keys, outdated libraries, or insecure modes like ECB.
Known attack vectors include:
-
Side-Channel Attacks – Instead of breaking AES mathematically, attackers may exploit physical information (like power usage, timing, or electromagnetic leaks) to recover keys.
-
Weak Implementations – Errors in how AES is coded (e.g., poor random number generation or weak key management) can make even strong encryption insecure.
-
Brute-Force Feasibility – With current technology, brute-forcing AES-128, AES-192, or AES-256 is impractical. However, advances in computing (such as quantum computing) are closely monitored.
-
Related-Key Attacks (theoretical) – Some academic research has shown very limited scenarios where related keys might reduce security, but these are not practical in real-world AES use.
Conclusion
The Advanced Encryption Standard AES has become the backbone of modern data protection. Its balance of strong security, efficiency, and adaptability makes it the preferred choice for governments, businesses, and everyday digital applications.
While no encryption method is entirely free from risks, AES has consistently stood the test of time against both practical and theoretical attacks. Its true strength lies not only in the algorithm itself but also in how securely it is implemented, managed, and integrated into systems.
In a world where data is one of the most valuable assets, AES plays a critical role in ensuring privacy, trust, and security. By understanding how it works and applying it correctly, organizations and individuals can stay protected in an increasingly connected digital landscape.



