The data encryption standard (DES) remains one of the most influential tools in the history of cryptography. More than just an algorithm, the data encryption standard provides a structured and reliable method for securing electronic information, enabling businesses, governments, and individuals to protect sensitive data from unauthorized access. In this clear and practical guide, we’ll explore the data encryption standard in detail — covering its meaning, how it works, historical background, core operations, strengths, weaknesses, and real-world applications, along with an easy-to-follow data encryption standard example to put the concept into perspective.
What Is the Data Encryption Standard (DES)?
The data encryption standard (DES) is one of the earliest and most well-known encryption methods in modern computing. In simple terms, the data encryption standard is a symmetric-key block cipher algorithm — meaning it uses the same secret key to both scramble (encrypt) and unscramble (decrypt) information.
Let’s break that down:
-
Symmetric-key → The same key is shared between the sender and receiver. If either party loses the key, the encrypted data becomes useless. See our Comprehensive Symmetric Encryption Guide.
-
Block cipher → Data is divided into fixed-size chunks (blocks), and each block is processed separately. In DES, each block is 64 bits long.
-
Encryption & Decryption → Encryption turns readable data into an unreadable format; decryption turns it back into its original form using the same key.
For example, if two people want to communicate securely, they both need the exact same DES key. Without that key, even if someone intercepts the data, it will appear as meaningless symbols — a principle at the heart of data encryption standard decryption.
Historically, DES was developed in the early 1970s by IBM in collaboration with the U.S. National Security Agency (NSA). It was officially adopted as a Federal Information Processing Standard (FIPS) in 1977 by the National Institute of Standards and Technology (NIST). The goal was clear: protect sensitive but unclassified government and commercial data from unauthorized access.
Although modern systems now use stronger algorithms, the data encryption standard laid the foundation for encryption standards we rely on today. It remains an important topic in cybersecurity education, especially for understanding how encryption evolved.
A Brief History of DES
Adopted as a U.S. federal standard in 1977, DES became the go-to encryption method for securing government, financial, and corporate data through the 1980s and 1990s. By the late 1990s, advances in computing made it increasingly vulnerable, leading to its gradual phase-out.
Key Features of the Data Encryption Standard
-
Block Cipher
DES works by dividing data into 64-bit blocks. Each block is treated separately during encryption and decryption. This means whether you’re encrypting a short message or a large file, DES processes it in fixed-size chunks. -
Key Length
The algorithm uses a 56-bit encryption key, plus 8 parity bits used for error detection. That makes 64 bits in total, though only the 56 bits actually influence the encryption process. -
Symmetry
DES is a symmetric-key algorithm, which means the same key is used for both encryption and DES decryption. If the key is lost or stolen, the security of the data is compromised.
Data Encryption Standard Example
Imagine Jane wants to send a confidential message to John. She uses the data encryption standard with a 56-bit key. Her original readable message (plaintext) is converted into an unreadable string of characters (ciphertext) through the process above. When John receives the message, he applies the same key to reverse the process — a perfect example of DES’s symmetric encryption method. Without that exact key, the message remains impossible to read.
The DES Encryption Algorithm: How It Works
The data encryption standard follows a systematic sequence:
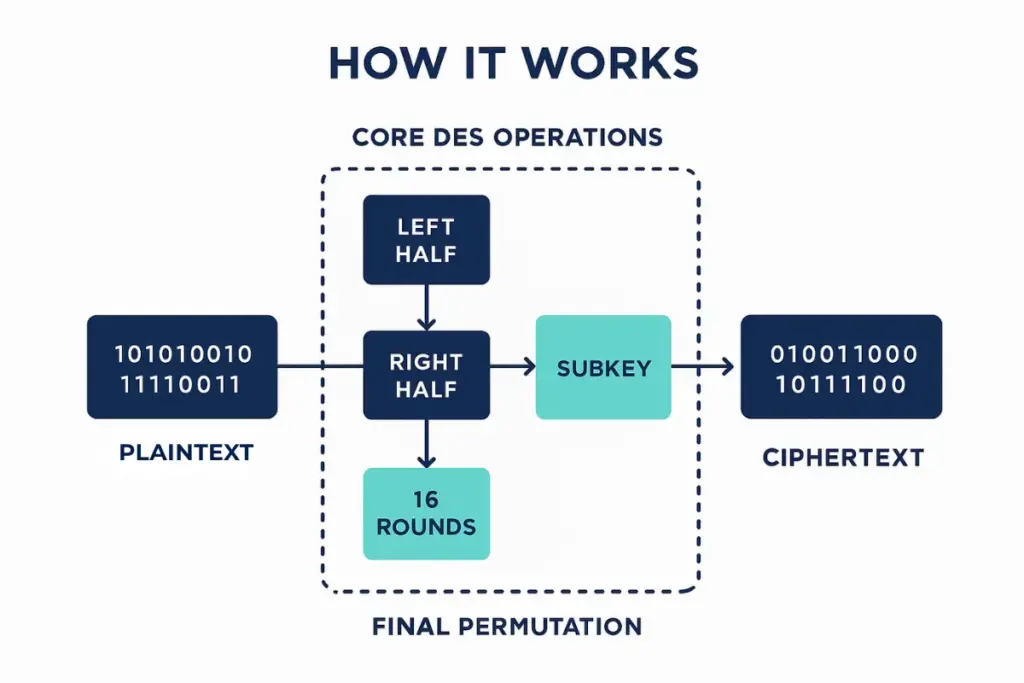
1. Initial Permutation (IP)
The 64-bit block of plaintext undergoes an initial bit-level permutation, rearranging the order of bits to set the stage for encryption.
2. Splitting the Data
The permuted block is split into two equal halves: a left half and a right half.
3. 16 Rounds of Processing
Each half goes through 16 rounds of operations involving:
- Expansion: The right half expands from 32 bits to 48 bits.
- Substitution (S-boxes): Groups of bits are substituted according to predefined tables, adding non-linearity to the process.
- Permutation: The bits are rearranged again to further obscure the data.
- Mixing with Subkeys: Each round uses a unique 48-bit subkey derived from the original key.
4. Subkey Generation
The original 56-bit key is shifted and permuted to produce sixteen 48-bit subkeys — one for each round of encryption.
5. Final Permutation (FP)
After all 16 rounds, the two halves are combined and a final permutation produces the ciphertext.
DES Decryption: How It Reverses Encryption
Data encryption standard decryption is the process of turning scrambled, unreadable ciphertext back into its original plaintext — and it works by following the exact reverse of the encryption steps.
In the data encryption standard program, the same secret key is used for both encryption and decryption (this is what makes DES a symmetric-key algorithm). When decrypting, the algorithm:
- Takes the ciphertext produced by the encryption phase.
- Applies the subkeys in the reverse order — round 16’s key is used first, and round 1’s key is used last
- Reverses each transformation (permutation, substitution, expansion, and mixing) step-by-step.
- Applies the final inverse permutation to reconstruct the original message.
Because the data encryption standard relies entirely on the correct key for both encryption and decryption, key management is critical. If the key is lost, there’s no “reset” or “password recovery” — the encrypted data is permanently inaccessible.
For example, if Jane encrypts a file using DES and loses her 56-bit key, not even the most powerful computer can retrieve her plaintext without trying every possible key combination — which is exactly why secure key storage is as important as the encryption process itself.
DES Security: Strengths, Weaknesses, and What Replaced It
While Data Encryption Standard (DES) provided a basic level of confidentiality, advances in computing power exposed its vulnerabilities. Understanding its strengths and weaknesses helps explain why it was eventually replaced by more robust encryption standards.
How Secure Was DES? A Technical Perspective
-
Key Space: With 2^56 possible keys (~72 quadrillion), DES provided strong protection in the 1970s but is small by today’s standards.
-
Attack Risk: Vulnerable to brute-force attacks with sufficient dedicated computing resources.
-
Cryptanalysis: Susceptible to techniques such as differential and linear cryptanalysis.
-
Current Recommendation: Not suitable for high-security applications; AES or other stronger algorithms are advised.
While DES is no longer secure for protecting sensitive data, it remains an important milestone in the history of cryptography — shaping how modern encryption is designed and evaluated.
Why DES Was Revolutionary
When introduced in 1977, the Data Encryption Standard was groundbreaking. It offered a widely available, government-approved method to protect electronic data — at a time when most organizations lacked any formal encryption protocol.
By providing a consistent, standardized framework, DES made secure communication and data storage practical for governments, banks, and businesses. Through the late 1970s to the 1990s, it became the gold standard for encrypting sensitive information — from financial transactions to corporate records — as digital data became central to daily operations.
Security Weaknesses and Decline
The main weakness of DES was its 56-bit key length. This was secure in the 1970s but became inadequate as computing power advanced.
A pivotal moment came in 1998, when the Electronic Frontier Foundation built a custom machine capable of cracking a DES key in under 24 hours. This demonstrated that DES could no longer protect high-value data against determined attackers.
Improvements Beyond DES: The Rise of Triple DES and AES
While the Data Encryption Standard was groundbreaking when it was introduced, advancements in computing power eventually made it vulnerable to brute-force attacks. To address these weaknesses, researchers developed an enhanced version known as the Triple Data Encryption Standard (Triple DES or 3DES).
Triple DES applies the DES algorithm three times in succession with multiple keys, making it significantly more secure than the original data encryption standard. This improvement extended the life of DES-based systems and ensured stronger protection for sensitive industries like banking, payments, and government communication.
However, 3DES came with performance drawbacks, especially in the age of high-speed internet and large-scale data processing. Eventually, the Advanced Encryption Standard (AES) replaced it as the U.S. government standard, offering key sizes of 128, 192, or 256 bits and stronger algorithmic design.
If you’re deciding between legacy DES and modern AES, see our comparison AES vs DES Encryption for a detailed breakdown of security, speed, and use cases.
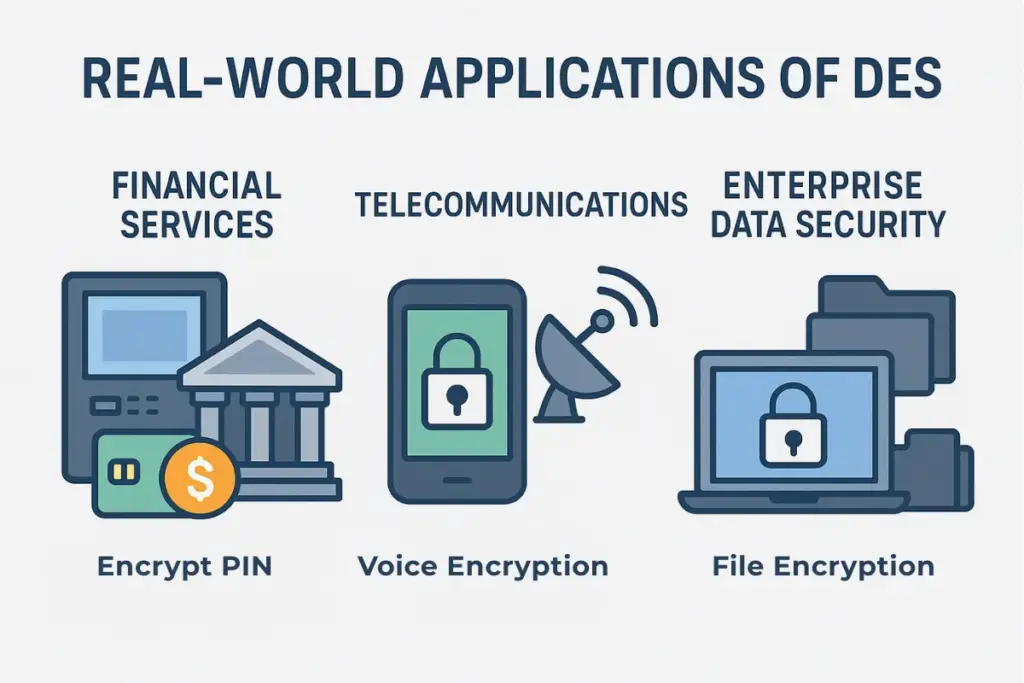
Real-World Applications of DES
The data encryption standard program may have been replaced by more advanced algorithms in most modern systems, but its impact on real-world security was massive. For decades, DES formed the backbone of encryption in industries where data confidentiality was critical. Here’s how it was applied in practice:
1. Financial Services
Banks, ATM networks, and payment processors were among the earliest adopters of DES. It was used to:
-
Encrypt PIN codes during ATM transactions.
-
Protect credit and debit card data sent over telephone lines.
-
Secure financial transfers between banks.
By implementing the data encryption standard program, banks could prevent criminals from intercepting and reading sensitive transaction information. Even today, some legacy ATM systems still use data encryption standard decryption to read older encrypted data.
2. Telecommunications
Before high-speed internet and fiber optics became the norm, telecom providers relied heavily on DES to secure communications over both public and private networks. Common uses included:
-
Voice encryption to prevent eavesdropping on calls.
-
Data encryption for files sent between offices or data centers.
-
Protecting signaling data that controlled network operations.
The simplicity and reliability of the data encryption standard made it an ideal choice for large-scale, continuous communication systems.
3. Enterprise Data Security
Large corporations used the data encryption standard to safeguard:
-
Stored files containing sensitive corporate data.
-
Regulatory compliance records.
-
Proprietary business information.
While modern businesses now rely on stronger algorithms like AES, DES remains important in certain backward-compatible systems and archived data. Understanding its operation also helps IT professionals grasp the foundations of symmetric encryption before moving to more advanced methods.
Why Learn About the Data Encryption Standard Today?
Studying DES remains relevant for several reasons:
- Legacy Systems: Many older infrastructures still use DES. Security professionals working with such systems need a solid understanding of the standard to maintain or migrate them securely.
- Cryptanalysis Training: DES serves as a foundational case study for learning and practicing cryptanalytic methods.
- Historical Perspective: The evolution of DES—from industry standard to obsolete—illustrates the lifecycle of cryptographic algorithms and how security requirements change over time.
Conclusion: Key Takeaways
The data encryption standard was a pioneering force in the history of digital security, showing the world how electronic information could be both protected and, eventually, compromised. Its introduction marked a turning point — making encryption accessible to governments, enterprises, and the public at a time when secure communication was far from guaranteed.
While its 56-bit key length and susceptibility to brute-force attacks have long since retired it from most real-world applications, the data encryption standard continues to hold value as a teaching tool and a historical milestone. Its structure — from block-based operations to symmetric key usage — laid the groundwork for stronger encryption standards like AES.
Whether you’re maintaining legacy systems, learning about data encryption standard decryption, or studying cryptographic algorithms in an academic setting, understanding DES offers a clearer perspective on the challenges and innovations that shape today’s encryption landscape. In short, DES is more than just a relic of the past — it’s a foundation upon which modern data security was built.
Further Reading
- Data Encryption Standard (FIPS 46-3)
- Data Encryption Standard on Wikipedia
- Electronic Frontier Foundation DES cracking demonstration



