Symmetric and asymmetric encryption are central to secure communication in today’s digital world. Organizations, businesses, and individuals rely on these cryptographic methods to protect sensitive data and ensure privacy online. But what is the real difference between symmetric and asymmetric encryption, and when should each be used? This article provides a comprehensive, direct comparison, giving you everything you need to confidently distinguish between symmetric and asymmetric encryption.
What is Symmetric Encryption?
Symmetric encryption uses a single secret key for both encrypting and decrypting the data. This method is known for its speed and simplicity. The main challenge is sharing the key securely between sender and receiver. Examples of symmetric ciphers include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and 3DES.
Symmetric encryption is best for encrypting large volumes of data, such as database backups, internal server communications, or file storage. Its computational efficiency is a significant advantage where performance is critical. For a broader introduction to these concepts, see our beginner’s guide to symmetric encryption.
How Symmetric Encryption Works
- Key Generation: A random secret key is generated.
- Encryption: Data is encrypted using this secret key.
- Decryption: Recipient uses the same secret key to decrypt and read the original data.
What is Asymmetric Encryption?
Unlike symmetric encryption, asymmetric encryption relies on a pair of cryptographic keys: a public key and a private key. The public key is shared openly, while the private key remains confidential with the owner. Data encrypted with the public key can only be decrypted using the corresponding private key, and vice versa.
Algorithms such as RSA, ECC (Elliptic Curve Cryptography), and DSA are widely used asymmetric encryption methods. Asymmetric encryption is slower but excels at securing key exchanges, digital signatures, and smaller data sets like credentials or session keys. Protocols like Diffie-Hellman key exchange often bootstrap secure symmetric keys over insecure channels.
How Asymmetric Encryption Works
- Key Pair Generation: Public and private keys are generated.
- Public Key Distribution: The public key is shared widely; the private key is kept secret.
- Encryption: Sender encrypts data using the recipient’s public key.
- Decryption: Recipient uses their private key to decrypt the data.
- Digital Signatures: Sender can sign data with their private key, and anyone can verify it with the public key.
Symmetric Key vs Asymmetric Key Encryption: Side-by-Side
-
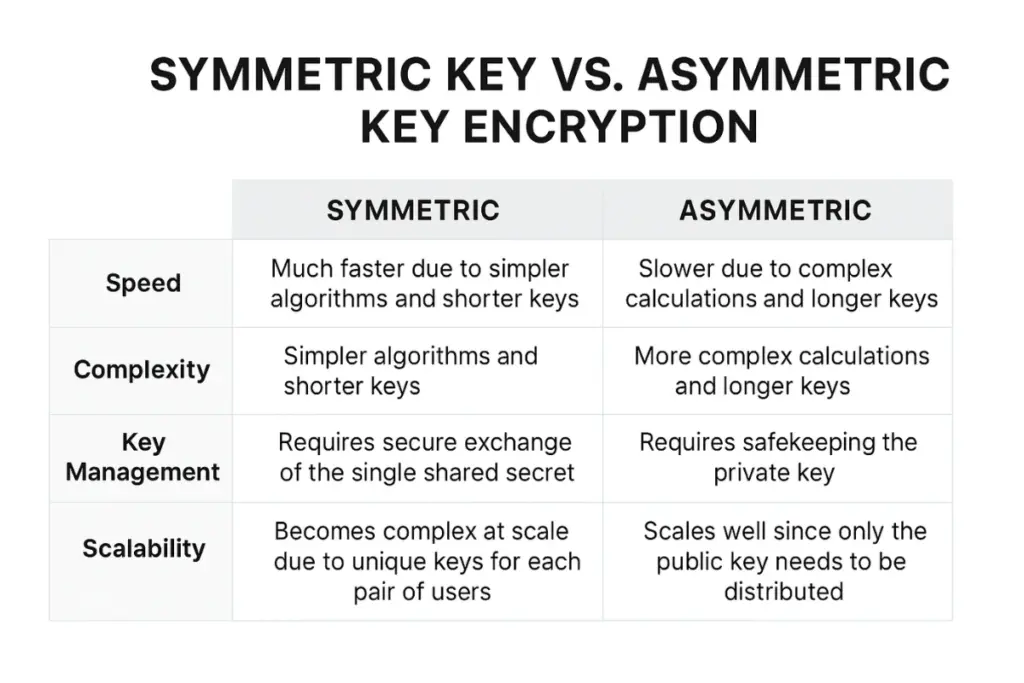
Speed: Symmetric key encryption operates significantly faster because it relies on simpler mathematical operations and shorter key lengths. This makes it ideal for encrypting large volumes of data, such as full disk encryption or streaming media.
-
Complexity: Asymmetric key encryption involves advanced mathematical functions like modular exponentiation or elliptic curves, which require more processing power. While this makes it slower, it provides enhanced security for activities such as secure key exchange, digital signatures, and authentication.
-
Key Management: Symmetric key encryption depends on a shared secret key, meaning both sender and receiver must have the same key—and this key must be exchanged securely. In contrast, asymmetric key encryption uses a pair of keys (public and private), so only the private key must remain confidential, reducing the risk during exchange.
-
Scalability: In symmetric systems, the number of keys grows rapidly with the number of participants (n users need n(n-1)/2 unique keys). Asymmetric encryption scales more efficiently because users only need to share their public keys, simplifying secure communication across large networks.
While AES outperforms DES in both security and speed, our AES vs. DES encryption comparison provides a deeper breakdown of their technical and practical differences.
Symmetric and Asymmetric Encryption: Difference in Security
The primary security distinction between symmetric and asymmetric encryption is in how they handle keys.
In symmetric encryption, the same secret key is used for both encryption and decryption, meaning its entire security depends on keeping that key confidential. If the key is intercepted or leaked, an attacker can instantly decrypt all past and future communications encrypted with it.
In asymmetric encryption, two keys are used: a public key (shared openly) and a private key (kept secret). The public key can be distributed freely without compromising security, since only the private key can decrypt the data. This eliminates the need to transmit the private key over any channel, drastically reducing the risk of key exposure.
Additionally, asymmetric encryption supports digital signatures and authentication, providing both confidentiality and data integrity. Symmetric encryption, while generally faster, must often be paired with integrity checks (like MACs) to prevent tampering.
Use Cases in Modern Technology
Symmetric Encryption
-
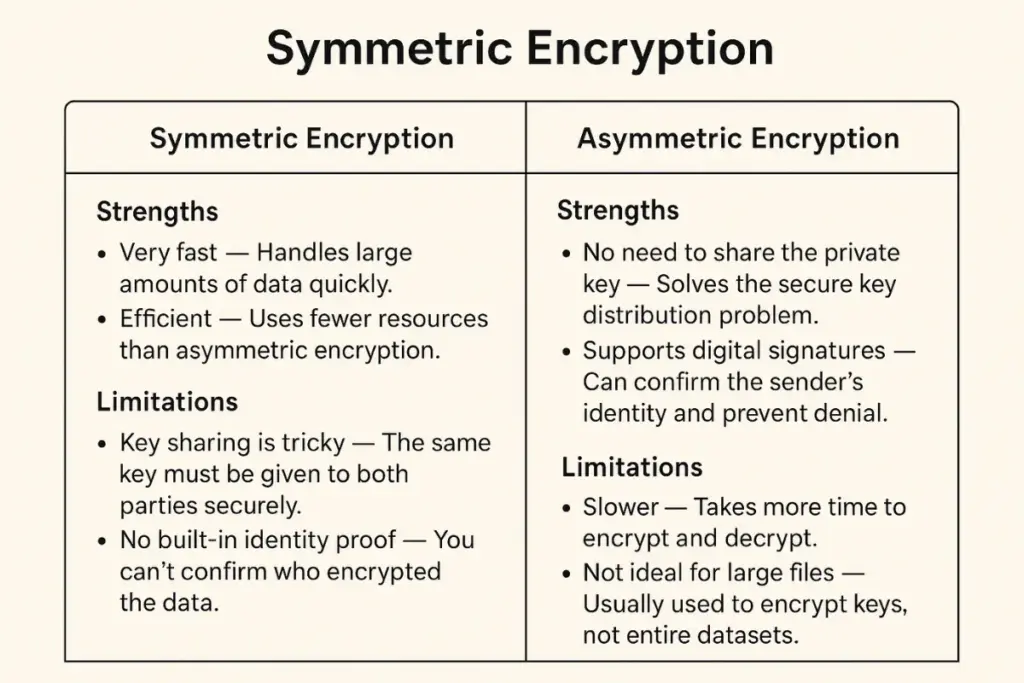
Bulk Data Storage – Used to encrypt large amounts of data efficiently, such as securing entire hard drives (full-disk encryption) or protecting sensitive database records. Its high speed makes it ideal for storage systems where quick access is essential.
-
VPNs and Secure Tunnels – Protects continuous data streams between endpoints, like in Virtual Private Networks or site-to-site tunnels, ensuring that all transmitted information remains confidential.
-
Fast Internal Communication – Enables secure data transfer between trusted servers within the same network or data center, where performance is critical and low latency is required.
Asymmetric Encryption
-
Secure Email – Encrypts emails so only the intended recipient, holding the corresponding private key, can read the message. Often used with protocols like PGP or S/MIME.
-
SSL/TLS Handshakes – Facilitates the secure exchange of information between a browser and a server, forming the foundation of HTTPS by negotiating keys without exposing sensitive credentials.
-
Digital Signatures & Authentication – Verifies the authenticity and integrity of data, such as confirming software updates come from a trusted source or validating blockchain transactions.
-
Key Exchange – Allows the secure sharing of a symmetric encryption key over an insecure channel, often serving as the first step before switching to faster symmetric encryption for the actual data transfer.
Symmetric and Asymmetric Encryption: Strengths and Limitations
Symmetric Encryption
Strengths
-
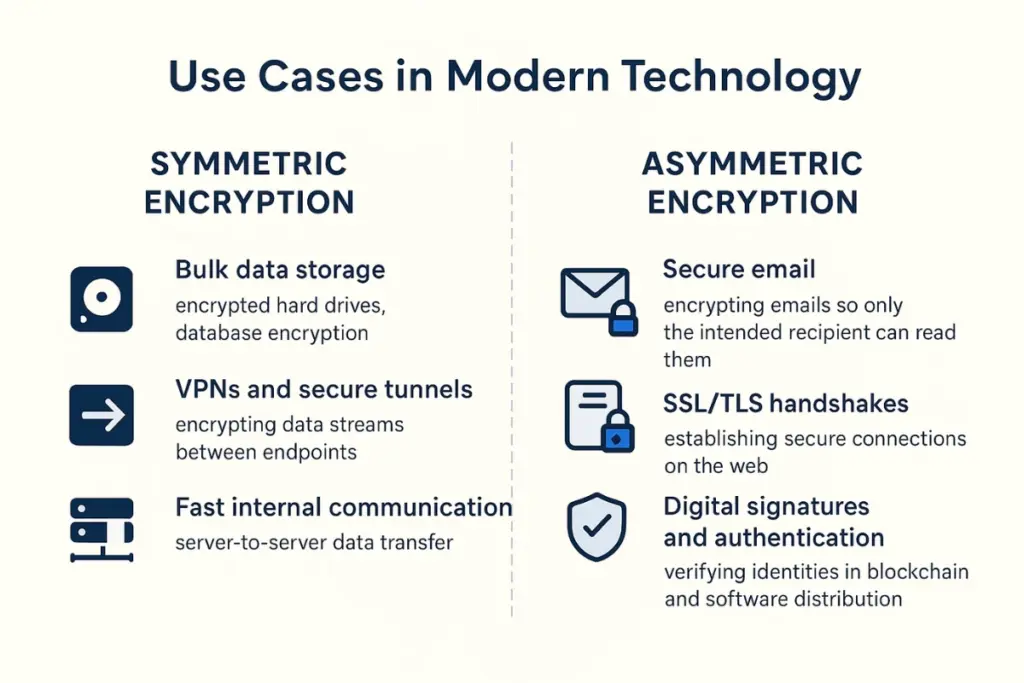
Very fast — Handles large amounts of data quickly.
-
Efficient — Uses fewer resources than asymmetric encryption.
Limitations
-
Key sharing is tricky — The same key must be given to both parties securely.
-
No built-in identity proof — You can’t confirm who encrypted the data.
Asymmetric Encryption
Strengths
-
No need to share the private key — Solves the secure key distribution problem.
-
Supports digital signatures — Can confirm the sender’s identity and prevent denial.
Limitations
-
Slower — Takes more time to encrypt and decrypt.
-
Not ideal for large files — Usually used to encrypt keys, not entire datasets.
-
Requires longer keys — Needs more bits for the same security strength as symmetric encryption.
Real-World Applications of Symmetric and Asymmetric Encryption
Encryption isn’t just a theoretical concept—it powers countless security mechanisms we use daily. From securing personal chats to verifying software integrity, both symmetric and asymmetric encryption methods serve distinct purposes depending on the context. The choice between them often balances speed, resource usage, and the need for secure key exchange.
- Encrypting payloads in messaging apps
In secure messaging platforms like WhatsApp, Signal, or Telegram, symmetric and asymmetric encryption plays a crucial role. When two users start a conversation, asymmetric encryption (RSA or Elliptic Curve) securely exchanges a shared secret key. Once this key is established, the app switches to symmetric encryption (often AES) to encrypt the actual messages. This approach keeps the communication both fast and secure, ensuring that even if someone intercepts the traffic, they can’t read the content without the shared key.
- Signing software and documents
When software companies release an update or a digital document, they need a way to prove it’s authentic and untampered. This is where asymmetric encryption steps in. Developers use a private key to create a digital signature, which is then attached to the software or file. Anyone can verify the authenticity using the developer’s public key—without being able to forge the signature themselves. This process not only confirms who created the file but also guarantees that the file hasn’t been altered since it was signed.
- Establishing secure web connections
Every time you connect to a website using HTTPS, a handshake occurs between your browser and the server to establish a secure communication channel. In this process, asymmetric encryption (RSA or ECDHE) is used to securely exchange a symmetric session key. Once the key is agreed upon, symmetric encryption—typically AES—takes over to protect all subsequent data transfer. This hybrid approach ensures strong security during the initial connection and high-speed encryption for the rest of the browsing session, making it the standard for secure web communication.
Transition to Hybrid Approaches
In the real world, very few encryption systems rely solely on symmetric or asymmetric encryption—they often use both in a complementary way. These hybrid systems are designed to combine the strengths of each approach while compensating for their weaknesses.
The process of combining symmetric and asymmetric encryption typically begins with asymmetric encryption (RSA, ECC, or ECDHE) to securely exchange a symmetric session key between two parties who have never met or shared secrets before. This session key—now safely transmitted—is then used for the remainder of the communication via symmetric encryption (commonly AES-256) to handle bulk data quickly and efficiently.
This workflow forms the backbone of SSL/TLS for secure websites, end-to-end encrypted messaging protocols like Signal or WhatsApp, and secure file transfer systems. The asymmetric step guarantees secure key distribution, even over an insecure network, while the symmetric phase ensures data can be encrypted and decrypted at high speed without performance bottlenecks.
The result is Maximum security without sacrificing efficiency. By blending the computational efficiency of symmetric algorithms with the secure key exchange of asymmetric cryptography, hybrid encryption models provide both speed and safety—making them the foundation for almost every secure communication protocol in use today.
Which to Use, and When?
The choice between symmetric and asymmetric encryption depends on what you’re protecting and how you plan to use it. Each approach excels in specific contexts:
Choose symmetric encryption when:
-
Encrypting large files or data streams: Symmetric algorithms like AES can handle gigabytes of data efficiently, making them ideal for databases, file backups, or media transfers.
-
Securing ongoing encrypted channels: Once a secure session key is in place (often exchanged via asymmetric methods), symmetric encryption ensures fast, low-latency communication for messaging apps, VPN tunnels, and real-time video calls.
Choose asymmetric encryption when:
-
Exchanging keys securely over an insecure network: Algorithms like RSA or Elliptic Curve Cryptography allow you to send a secret key to another party without prior contact, eliminating the risk of interception during key setup.
-
Authenticating identities and preventing forgery: Digital signatures generated with asymmetric keys verify that software, emails, or documents truly came from the claimed sender and haven’t been altered.
-
Encrypting small messages or credentials where speed is not critical: For sensitive but short data—like login tokens or configuration secrets—performance overhead is negligible compared to the added security benefits.
In many modern systems, you don’t actually have to choose just one—hybrid encryption combines both, using asymmetric methods for secure key exchange and symmetric methods for high-speed bulk encryption.
Conclusion: The Key Difference Between Symmetric and Asymmetric Encryption
Understanding how symmetric and asymmetric encryption work and their differences is essential for effective cybersecurity. Symmetric encryption brings speed, while asymmetric encryption secures communications where key exchange and identity are paramount. The difference between symmetric and asymmetric encryption lies in their distinct approaches to key management, speed, and scalability. Applying each appropriately ensures robust data protection, privacy, and safe digital communications.
Further Reading
- NIST Special Publication on AES Encryption Standard
- OWASP Cryptographic Storage Cheat Sheet
- FreeCodeCamp: Symmetric and Asymmetric Encryption
- Cloudflare Blog – TLS 1.3 Deep Dive