Symmetric Encryption Algorithm: A Clear Guide for Beginners
In this comprehensive guide, we’ll explore everything you need to know about symmetric encryption algorithms, from basic concepts to real-world applications, ensuring you gain a thorough understanding of this essential security technology.
What Is Symmetric Encryption?
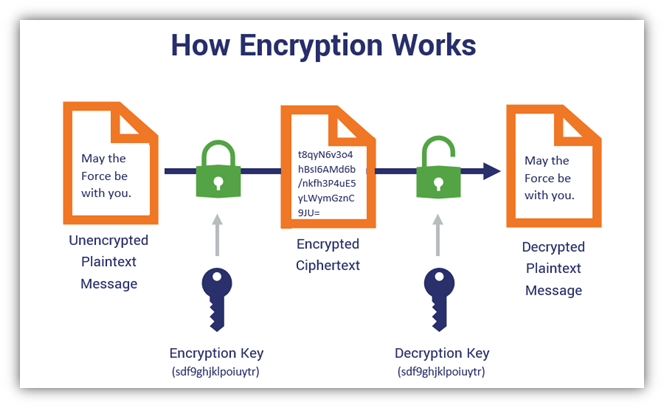
Symmetric encryption represents one of the oldest and most fundamental approaches to data protection. This cryptographic method uses a single shared key for both encrypting and decrypting information. Unlike asymmetric encryption, which employs different keys for encryption and decryption, symmetric encryption relies on the same secret key throughout the entire process.
The beauty of symmetric encryption lies in its simplicity and efficiency. When Alice wants to send a secure message to Bob, she encrypts the message using their shared secret key. Bob then uses the identical key to decrypt and read the message. This straightforward approach makes symmetric encryption incredibly fast and resource-efficient, which explains why it forms the backbone of many modern security systems.
The term “symmetric” perfectly describes this encryption method because both parties mirror each other’s actions using the same cryptographic key. This symmetry creates a balanced and efficient system for protecting sensitive information across various digital platforms.
How Symmetric Encryption Works
The process of symmetric encryption follows a clear and logical sequence. First, the sender and receiver must securely establish a shared secret key. This key serves as the foundation for all subsequent encrypted communications between the parties.
During encryption, the algorithm takes the original plaintext message and applies mathematical transformations using the secret key. These transformations scramble the data into an unreadable format called ciphertext. The specific mathematical operations depend on the chosen encryption algorithm, but they all share the common goal of making the data incomprehensible to unauthorized observers.
For decryption, the process reverses exactly. The recipient applies the same algorithm using the identical secret key to transform the ciphertext back into readable plaintext. This reversible process ensures that only parties possessing the correct key can access the original information.
The strength of symmetric encryption depends heavily on key management. The secret key must remain confidential and be shared only between authorized parties. If an attacker gains access to the key, the entire encryption scheme becomes compromised, highlighting the critical importance of secure key distribution and storage.
Types of Symmetric Encryption Algorithms
Block Ciphers
Block ciphers process data in fixed-size blocks, typically 64 or 128 bits at a time. These algorithms divide the plaintext into blocks and encrypt each block separately using the secret key. Popular block ciphers include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES.
AES stands as the most widely adopted block cipher today, offering three key lengths: 128, 192, and 256 bits. Government agencies, financial institutions, and technology companies rely on AES for protecting classified and sensitive information due to its robust security and efficient performance.
Stream Ciphers
Stream ciphers encrypt data one bit or byte at a time, creating a continuous stream of encrypted output. These algorithms generate a pseudorandom keystream that combines with the plaintext to produce ciphertext. Stream ciphers excel in real-time applications where data arrives continuously, such as voice communications and video streaming.
RC4 represents one of the most famous stream ciphers, though security vulnerabilities have led to its deprecation in favor of more secure alternatives like ChaCha20. Stream ciphers typically offer faster encryption speeds for certain applications but require careful implementation to maintain security.
Key Management in Symmetric Encryption
Effective key management forms the cornerstone of any successful symmetric encryption implementation. Organizations must establish robust processes for key generation, distribution, storage, rotation, and destruction to maintain security throughout the encryption lifecycle.
Key generation requires high-quality random number generators to ensure unpredictability. Weak or predictable keys can render even the strongest encryption algorithms vulnerable to attack. Modern systems employ hardware-based random number generators or cryptographically secure pseudorandom number generators to create strong encryption keys.
Key distribution presents one of the greatest challenges in symmetric encryption. Since both parties need the same key, organizations must find secure channels for sharing these secrets. Common approaches include using secure key exchange protocols, physical delivery methods, or pre-shared key agreements established through secure channels.
Regular key rotation enhances security by limiting the amount of data encrypted under any single key. If an attacker compromises a key, rotation minimizes the potential damage by ensuring that only a limited dataset remains vulnerable. Industry best practices recommend rotating encryption keys based on factors such as data sensitivity, usage patterns, and regulatory requirements.
Advantages of Symmetric Encryption
Symmetric encryption offers several compelling advantages that explain its widespread adoption across various industries and applications. Speed represents perhaps the most significant benefit, as symmetric algorithms can encrypt and decrypt data much faster than their asymmetric counterparts. This performance advantage becomes crucial in high-throughput environments where large volumes of data require protection.
Resource efficiency makes symmetric encryption ideal for devices with limited computational power. Mobile devices, IoT sensors, and embedded systems benefit from the low processing overhead required by symmetric algorithms. This efficiency enables real-time encryption without significantly impacting system performance.
Proven security gives organizations confidence in symmetric encryption’s ability to protect sensitive data. Algorithms like AES have undergone extensive cryptanalytic scrutiny and remain unbroken despite years of analysis by security researchers worldwide. This track record provides assurance that properly implemented symmetric encryption can effectively safeguard information.
Simplicity in implementation reduces the likelihood of security vulnerabilities caused by coding errors. The straightforward nature of symmetric encryption makes it easier for developers to implement correctly, reducing the risk of introducing weaknesses through poor programming practices.
Disadvantages and Limitations
Despite its numerous advantages, symmetric encryption faces several inherent limitations that organizations must consider when designing security systems. The key distribution problem represents the most significant challenge, as both parties must somehow obtain the same secret key through a secure channel. This requirement can create logistical difficulties, especially when establishing communications with new parties or managing large numbers of encryption relationships.
Scalability issues arise when organizations need to provide secure communications between many different parties. With symmetric encryption, each pair of communicating parties requires a unique shared key, leading to a quadratic growth in the number of keys as the organization expands. Managing hundreds or thousands of encryption keys becomes increasingly complex and error-prone.
Lack of non-repudiation means that symmetric encryption cannot prove the identity of message senders. Since both parties possess the same key, either party could theoretically have created any given encrypted message. This limitation makes symmetric encryption unsuitable for applications requiring digital signatures or proof of message origin.
Key compromise consequences can be severe, as losing control of a symmetric key immediately compromises all data encrypted with that key. Unlike asymmetric systems where compromising one key doesn’t necessarily affect others, symmetric key compromise requires immediate action to prevent unauthorized data access.
Real-World Applications
Symmetric encryption powers countless applications in our daily digital lives. Banking systems rely heavily on symmetric encryption to protect financial transactions and customer data. When you use an ATM or make an online purchase, symmetric algorithms likely safeguard your sensitive financial information during transmission and storage.
Virtual Private Networks (VPNs) extensively use symmetric encryption to create secure tunnels over public internet connections. These systems establish shared keys through initial handshake protocols, then use symmetric algorithms to encrypt all subsequent communications at high speeds.
File and disk encryption utilities employ symmetric algorithms to protect data at rest. When you encrypt files on your computer or use full-disk encryption, symmetric algorithms like AES provide the underlying protection while maintaining reasonable performance for everyday operations.
Secure messaging applications implement symmetric encryption to protect user conversations. After establishing shared keys through secure protocols, these applications use symmetric algorithms to encrypt messages quickly and efficiently while preserving battery life on mobile devices.
Common Symmetric Encryption Algorithms
AES (Advanced Encryption Standard) dominates the modern symmetric encryption landscape. Adopted by the U.S. government in 2001, AES supports key lengths of 128, 192, and 256 bits, with longer keys providing enhanced security at the cost of slightly reduced performance. AES-256 is particularly popular for protecting highly sensitive data due to its exceptional security margins.
DES (Data Encryption Standard), while historically significant, is now considered obsolete due to its 56-bit key length, which modern computers can break through brute force attacks. However, understanding DES remains valuable for educational purposes and historical context.
Triple DES (3DES) emerged as a interim solution to DES’s security limitations by applying the DES algorithm three times with different keys. While more secure than DES, 3DES is being phased out in favor of AES due to performance considerations and security margins.
Blowfish and Twofish represent alternative symmetric algorithms designed by Bruce Schneier. These algorithms offer good security and performance characteristics, though they haven’t achieved the widespread adoption of AES.
An Example of Symmetric Encryption in Practice
To illustrate how symmetric encryption works in practice, consider a simple example of symmetric encryption using a basic substitution cipher. While not cryptographically secure, this example demonstrates the fundamental principles clearly.
Imagine Alice wants to send the message “HELLO” to Bob using a simple symmetric cipher. They agree on a shared key: shift each letter by 3 positions in the alphabet. Using this key, Alice encrypts her message:
H → K, E → H, L → O, L → O, O → R
The encrypted message becomes “KHOOR.” Alice sends this ciphertext to Bob, who applies the reverse operation using the same key (shift back by 3 positions) to recover the original message “HELLO.”
In real-world applications, modern symmetric encryption algorithms use complex mathematical operations involving substitution, permutation, and key mixing to create cryptographically secure transformations that resist attack even with powerful computers.
Security Considerations
Implementing secure symmetric encryption requires attention to numerous security considerations beyond simply choosing a strong algorithm. Key length directly impacts security strength, with longer keys providing exponentially greater resistance to brute force attacks. However, organizations must balance security requirements with performance needs and system constraints.
Mode of operation affects how block ciphers handle data longer than a single block. Common modes include Electronic Codebook (ECB), Cipher Block Chaining (CBC), and Galois/Counter Mode (GCM). Each mode offers different security properties and performance characteristics, making mode selection crucial for overall system security.
Side-channel attacks represent a significant threat to symmetric encryption implementations. These attacks exploit information leaked through timing variations, power consumption patterns, or electromagnetic emissions during encryption operations. Protecting against side-channel attacks requires careful implementation and may involve countermeasures like constant-time algorithms and power analysis resistance.
Quantum computing poses a future threat to symmetric encryption, though the impact is less severe than for asymmetric algorithms. While quantum computers could theoretically reduce the effective security of symmetric keys by half, doubling key lengths provides adequate protection against this threat.
Future of Symmetric Encryption
The future of symmetric encryption looks robust, with ongoing research focused on improving performance, security, and resistance to emerging threats. Post-quantum cryptography initiatives are evaluating how symmetric algorithms will fare against quantum computing attacks and developing guidelines for quantum-resistant implementations.
Lightweight cryptography represents an active research area addressing the needs of resource-constrained devices in the Internet of Things. These specialized symmetric algorithms optimize for minimal power consumption, small code size, and low computational requirements while maintaining adequate security.
Homomorphic encryption, while primarily an asymmetric technique, incorporates symmetric elements and enables computations on encrypted data without decryption. This emerging field could revolutionize cloud computing and privacy-preserving analytics.
As cyber threats continue evolving, symmetric encryption algorithms will adapt to meet new challenges while maintaining their fundamental advantages of speed, efficiency, and proven security. Organizations investing in symmetric encryption today can expect these technologies to remain relevant and effective for protecting sensitive data well into the future.
Symmetric encryption algorithm implementation requires careful consideration of algorithm selection, key management practices, and security requirements. By understanding these fundamental concepts and best practices, organizations can effectively leverage symmetric encryption to protect their most valuable digital assets while maintaining operational efficiency and performance.