Symmetric Encryption Algorithm: A Clear Guide for Beginners
Symmetric Encryption Algorithm: A Clear Guide for Beginners
In the world of cybersecurity, symmetric encryption algorithm plays a pivotal role in securing data. Whether you’re a beginner or just curious about how encryption works, this guide will break down the concept of symmetric encryption in simple terms. By the end, you’ll understand what a symmetric encryption algorithm is, how it works, and even see an example of symmetric encryption in action.
What Is Symmetric Encryption?
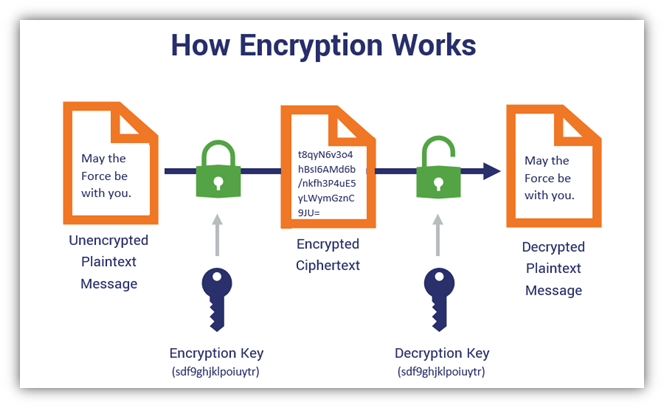
Symmetric encryption is a method of encrypting data where the same key is used for both encryption and decryption. This means that the sender and receiver must share the key securely. The simplicity and speed of symmetric encryption make it a popular choice for securing large amounts of data.
How Does a Symmetric Encryption Algorithm Work?
A symmetric encryption algorithm follows these basic steps:
- Key Generation: A secret key is generated, which will be used for both encryption and decryption.
- Encryption: The plaintext (original data) is converted into ciphertext (encrypted data) using the secret key.
- Decryption: The ciphertext is converted back into plaintext using the same secret key.
Because the same key is used for both processes, the symmetric encryption algorithm is efficient but requires careful key management.
Example of Symmetric Encryption
Let’s look at an example of symmetric encryption to make things clearer. Suppose Alice wants to send a confidential message to Bob. They both agree on a secret key beforehand. Alice uses the key to encrypt the message, and Bob uses the same key to decrypt it. Without the key, the message remains unreadable.
Advantages of Symmetric Encryption
- Speed: Symmetric encryption is faster than asymmetric encryption, making it ideal for encrypting large datasets.
- Simplicity: The process is straightforward, with only one key to manage.
Disadvantages of Symmetric Encryption
- Key Distribution: The biggest challenge is securely sharing the key between parties.
- Scalability: Managing keys becomes difficult as the number of users increases.
Common Symmetric Encryption Algorithms
Several symmetric encryption algorithms are widely used today, including:
- AES (Advanced Encryption Standard): The gold standard for symmetric encryption, used by governments and organizations worldwide. https://md-5.com?p=766
- DES (Data Encryption Standard): An older algorithm, now considered less secure due to its small key size. https://md-5.com?p=764
- 3DES (Triple DES): An improved version of DES, applying the algorithm three times for better security. https://md-5.com?p=765
For an in-depth comparison between AES and DES, see https://md-5.com?p=767.
Best Practices for Using Symmetric Encryption
To maximize the effectiveness of a symmetric encryption algorithm, follow these best practices:
- Use Strong Keys: Generate keys with sufficient length and randomness.
- Secure Key Exchange: Use secure channels or protocols (like TLS) to share keys. https://md-5.com?p=782
- Regularly Update Keys: Rotate keys periodically to minimize the risk of compromise.
Conclusion
Understanding symmetric encryption is essential for anyone interested in cybersecurity. By learning how a symmetric encryption algorithm works and its practical applications, you can better appreciate its role in protecting data. Whether you’re encrypting files, securing communications, or safeguarding sensitive information, symmetric encryption is a powerful tool in your arsenal.