Symmetric Encryption Algorithm: A Clear Guide for Beginners
What Is Symmetric Encryption?
Symmetric encryption algorithm is a foundational cornerstone of cryptography, playing a crucial role in protecting digital information. In this guide, you’ll gain a clear and thorough understanding of symmetric encryption, how it works, why it’s used, its strengths and limitations, and real-world practicalities. By reading further, you’ll understand not just the basics, but also in-depth details with minimal jargon and maximum clarity.
Introduction: The Core of Data Security
As cyber threats evolve, data protection is no longer optional—it’s essential. At the heart of secure data exchange lies symmetric encryption Learn how symmetric encryption works. This type of cryptography has helped secure everything from ancient codes to today’s online banking and file transfers. In a world constantly sharing sensitive information, knowing how symmetric encryption works empowers you to understand, trust, and even implement your own secure systems.
Symmetric Encryption: The Basics
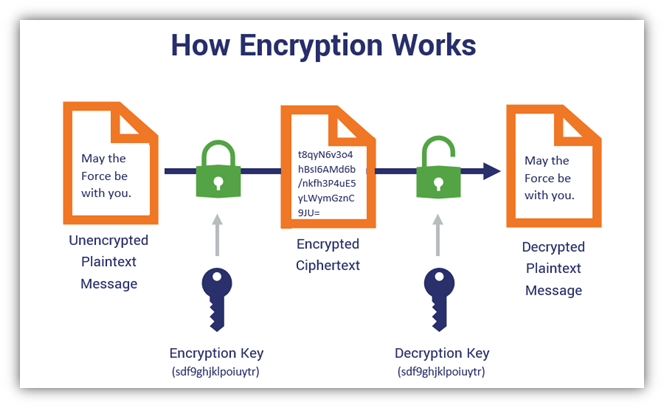
Symmetric encryption uses a single secret key for both encrypting and decrypting data. This differs from asymmetric encryption, where two separate keys (public and private) are used. In symmetric encryption, both the sender and receiver must have access to the same secret key, making key management a central issue.
Main Characteristics
- One secret key: Both encrypting and decrypting require the same key.
- Speed and efficiency: Symmetric encryption algorithms are faster than asymmetric counterparts.
- Data confidentiality: Protects data from unauthorized access.
- Key management challenge: Both parties must keep the key secure and never expose it during transit or storage.
How Does Symmetric Encryption Work?
Symmetric encryption algorithms transform readable data (plaintext) into unreadable form (ciphertext) using a secret key. The recipient, with the same key, reverts it back to plaintext through decryption.
The process unfolds in these steps:
- A secret key is generated and shared securely between the sender and receiver.
- The sender uses the key and a symmetric encryption algorithm to convert plaintext into ciphertext, rendering it incomprehensible to outsiders.
- The recipient uses the same key and algorithm to decrypt the ciphertext, restoring the original message.
Types of Symmetric Encryption Algorithms
Various algorithms have been developed for symmetric encryption, each balancing security, speed, and application needs.
1. Data Encryption Standard (DES)
- Oldest widely adopted symmetric encryption algorithm. Learn more about DES.
- 56-bit key; vulnerable to brute-force attacks today.
2. Triple DES (3DES)
- Improved DES by applying it three times with different keys (increasing security). Discover Triple DES details.
3. Advanced Encryption Standard (AES)
- The gold standard for modern symmetric encryption—used globally by governments and enterprises. Explore AES in-depth.
- Supports key sizes of 128, 192, and 256 bits.
- Fast, secure, suitable for large-scale applications and embedded systems.
4. Blowfish
- Flexible, fast cipher. See how Blowfish works.
- Simple design, commonly used in embedded systems and software.
5. RC4, RC5, and RC6
- Popular stream (RC4) and block ciphers (RC5, RC6) developed by RSA Security.
- RC4 is now considered insecure, but others remain in use for specific applications.
Real-World Example of Symmetric Encryption
Suppose Alice needs to send a confidential document to Bob. Alice and Bob agree in advance to use a secret key. Alice encrypts the document using Advanced Encryption Standard (AES) with their pre-shared key. She sends the encrypted file to Bob. Only Bob, who knows the symmetric key, can decrypt and read the contents. Anyone intercepting the data sees only scrambled characters.
When to Use Symmetric Encryption
Symmetric encryption is the default for high-speed, bulk data encryption. It excels when:
- Large volumes of data need to be processed rapidly.
- Secure channels exist to share keys in advance.
- Devices have limited computational power (IoT, smart cards, embedded devices).
Network protocols such as SSL/TLS (for HTTPS), file encryption tools, and disk encryption solutions rely heavily on symmetric encryption for high-speed operations.
Why Key Management Matters
The strongest symmetric encryption algorithm is only as secure as key management practices. If the secret key is intercepted or leaked, all encrypted data becomes accessible. Best practices for key management include:
- Limit key exposure: Use the shortest reasonable key distribution window.
- Never share keys openly: Use secure channels for sharing.
- Rotate keys regularly: Mitigate the risk of exposure.
- Store keys securely: Use hardware security modules or encrypted vaults.
Strengths and Weaknesses
Advantages
- Efficiency: Fast and minimal in computational overhead.
- Simplicity: Uses a single key, making the process straightforward.
- Scalability: Suitable for encrypting large amounts of data efficiently.
Limitations
- Key distribution problem: Securely sharing and managing the key is a constant challenge.
- No non-repudiation: Since both parties use the same key, verifying message origin is impossible.
- Less suitable for open, public networks: More complex solutions (asymmetric encryption) are often layered on top for key exchange.
Symmetric vs Asymmetric Encryption
For a deeper comparison, see our post on symmetric vs asymmetric encryption. While both aim to secure data, they differ substantially:
- Symmetric: One key for both operations. Fast, but needs secure key exchange.
- Asymmetric: Uses a public/private key pair. Slower but solves the key distribution problem.
Modern cryptosystems often use asymmetric encryption to exchange the symmetric key, after which all data is encrypted with symmetric methods. This hybrid approach takes advantage of both systems’ strengths.
Security of Symmetric Encryption Algorithms
The effectiveness of a symmetric encryption algorithm depends on the key size and the algorithm’s resistance to cryptanalysis (attack techniques). For example:
- DES: Now considered weak due to short key length.
- AES: Recognized as secure when used with sufficiently long keys, 128 bits or greater.
Attacks that symmetric encryption must resist include:
- Brute-force attacks: Trying all possible keys
- Cryptanalysis: Analyzing ciphertext to deduce the key
The solution to brute-force attacks is longer keys; modern standards recommend at least 128 bits.
Practical Applications in Everyday Life
Symmetric encryption is everywhere. It’s embedded into technologies many use daily:
- Wi-Fi networks: Use WPA2 and WPA3, which rely on AES.
- Credit card transactions: Safeguard transmitted data during purchases.
- File compression tools: Like WinZip, which can use AES for encryption.
- Full disk encryption: Windows BitLocker, Apple FileVault utilize symmetric encryption.
- Cloud storage: Providers offer encrypted spaces using symmetric keys for data protection.
Steps to Implement Symmetric Encryption
For application developers and IT professionals, implementing symmetric encryption securely involves:
- Choose the right algorithm: Opt for AES or another vetted symmetric encryption algorithm.
- Generate secure keys: Always use robust random number generators.
- Securely share keys: Use secure channels (asymmetric encryption or physical delivery if offline).
- Encrypt data: Use vetted libraries—avoid home-grown crypto solutions.
- Rotate and revoke keys as needed: Especially if there’s any suspicion of compromise.
- Audit and monitor: Regular checks can help detect key misuse.
Common Questions Answered
Is symmetric encryption still safe?
Absolutely—if state-of-the-art symmetric encryption algorithm and best practices for key management are used. AES-256, for example, is considered highly secure.
How do you securely share the symmetric key?
Use asymmetric encryption methods (such as RSA) or dedicated protocols (like Diffie-Hellman) for secure key exchange. Never share keys via insecure email, plaintext messages, or unprotected cloud services.
Can symmetric encryption be combined with other types?
Yes. A hybrid system using asymmetric methods for key exchange and symmetric for data encryption is standard practice in protocols such as SSL/TLS.
The Future of Symmetric Encryption
Ongoing research and advances in quantum computing present both opportunities and threats to symmetric encryption. For now, increasing key lengths and algorithm robustness ensure the continued use and security of symmetric encryption algorithms. Quantum-safe versions are under active development.
Conclusion
Understanding the symmetric encryption algorithm is vital for anyone concerned with information security. Whether you are a developer, IT professional, or privacy-conscious user, knowing its operation, strengths, limitations, and best practices arms you for the digital age. Effective key management and using modern encryption standards—most notably AES—should be paramount in your approach to data protection. As technology evolves, symmetric encryption will remain a core component of robust cybersecurity strategies.