Symmetric encryption algorithm plays a crucial role in safeguarding data, ensuring only authorized parties access sensitive information. Understanding this algorithm’s mechanisms is essential for anyone interested in cyber security, networking, or data privacy. This guide thoroughly explains what symmetric encryption algorithm is, how it works, practical use cases, strong examples, their advantages, limitations, and best practices for beginners and aspiring professionals.
What is Symmetric Encryption Algorithm?
Symmetric encryption algorithm uses the same secret key for both encrypting and decrypting data. This means the sender and the recipient must possess identical keys, making the process fast and efficient. Imagine you have a box with a special lock, and both you and your friend have the same key to open it. When you put a message inside and lock it, your friend can use the exact same key to open the box and read it.
Because only one key is involved, both the sender and the receiver must have identical copies of this key — and they must keep it safe from anyone else. If the key falls into the wrong hands, that person can both read and create messages that seem legitimate.
One of the biggest advantages of symmetric encryption is speed. Since it uses a single key, the process requires fewer computing resources, making it much faster than asymmetric encryption algorithm, which relies on two keys (a public key and a private key). This efficiency makes symmetric encryption algorithms ideal for encrypting large amounts of data quickly — such as files, databases, or communication between systems.
However, there’s one challenge: key sharing. Before any secure communication can begin, the secret key has to be exchanged between the parties in a secure way. If someone intercepts it during this exchange, they can access the encrypted data. That’s why symmetric encryption algorithm is often combined with other techniques for safe key distribution.
Popular symmetric encryption algorithm include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and Blowfish, all widely used to protect sensitive information in various applications.
Core Concepts and Terminology
To understand symmetric encryption algorithms, it’s important to first get familiar with some key terms:
-
Plaintext:
This is the original data or message in its readable and understandable form. Before encryption, all information—whether it’s text, files, or communication—is considered plaintext. For example, an email you write or a file you save is plaintext before it gets encrypted. -
Ciphertext:
After the encryption process, plaintext is transformed into ciphertext—a scrambled, unreadable format that protects the information from unauthorized access. Without the correct key to decrypt it, ciphertext appears as random gibberish and cannot be understood. -
Key:
The key is a secret value that both encrypts the plaintext into ciphertext and decrypts ciphertext back to plaintext. In symmetric encryption algorithm, the same key is used for both processes, so keeping this key secure is essential to maintaining data privacy. -
Block Cipher:
Block ciphers encrypt data in fixed-size blocks, such as 64 or 128 bits, processing one block at a time. Popular block ciphers include algorithms like AES (Advanced Encryption Standard) and DES (Data Encryption Standard). These ciphers often use special modes of operation to securely encrypt data larger than a single block. -
Stream Cipher:
Unlike block ciphers, stream ciphers encrypt data one bit or byte at a time. This makes them well-suited for applications where data comes in a continuous stream, such as secure voice or video communication. Examples include RC4 and Salsa20.
Understanding these core concepts and terms is crucial for grasping how different types of symmetric encryption algorithms work and why they are chosen for various security needs. With this foundation, you’ll better appreciate the strengths and applications of each encryption method discussed later in this article.
Popular Example of Symmetric Encryption
One of the most well-known and widely trusted symmetric encryption algorithms is AES (Advanced Encryption Standard). AES works by encrypting data in fixed-size blocks (commonly 128 bits) using a shared secret key that both the sender and receiver possess.
It has become the global standard for protecting sensitive information because it offers a strong balance of security, speed, and efficiency. Governments use AES to secure classified data, financial institutions rely on it for transactions, and everyday devices — from smartphones to Wi-Fi routers — implement AES to keep personal information safe.
AES is also highly versatile, supporting key sizes of 128, 192, or 256 bits, which allows users to choose between faster performance or even greater security depending on their needs. Its design makes it resistant to all known practical attacks, making it a cornerstone of modern data encryption.
Think of AES like a super-advanced safe that only opens if two people have the exact same key. The safe is built so well that even with all the tools in the world, breaking in would take thousands of years — so long that it’s practically impossible.
How Symmetric Encryption Algorithm Works
The fundamental workflow of symmetric encryption algorithm involves:
- Key Generation: A unique, secret key is generated.
- Encryption: Plaintext data is converted into ciphertext using the key.
- Decryption: The same key is used to reverse the process, restoring the original plaintext.
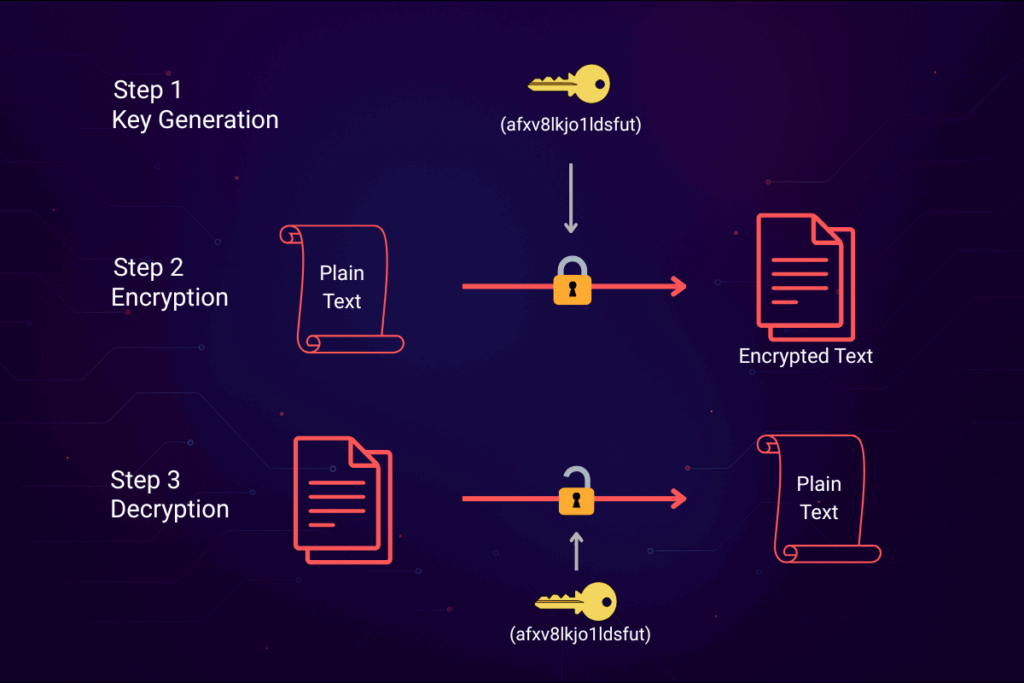
This streamlined approach makes symmetric encryption algorithms ideal for real-time applications such as disk encryption, secure messaging, and VPNs. Its efficiency is a major advantage, but secure key management is critical—if the key is exposed, all encrypted data can be compromised.
Common Applications of Symmetric Encryption
Symmetric encryption powers much of the security we rely on daily—whether shopping online, managing finances, or simply browsing the web. Here are some of its key real-world uses:
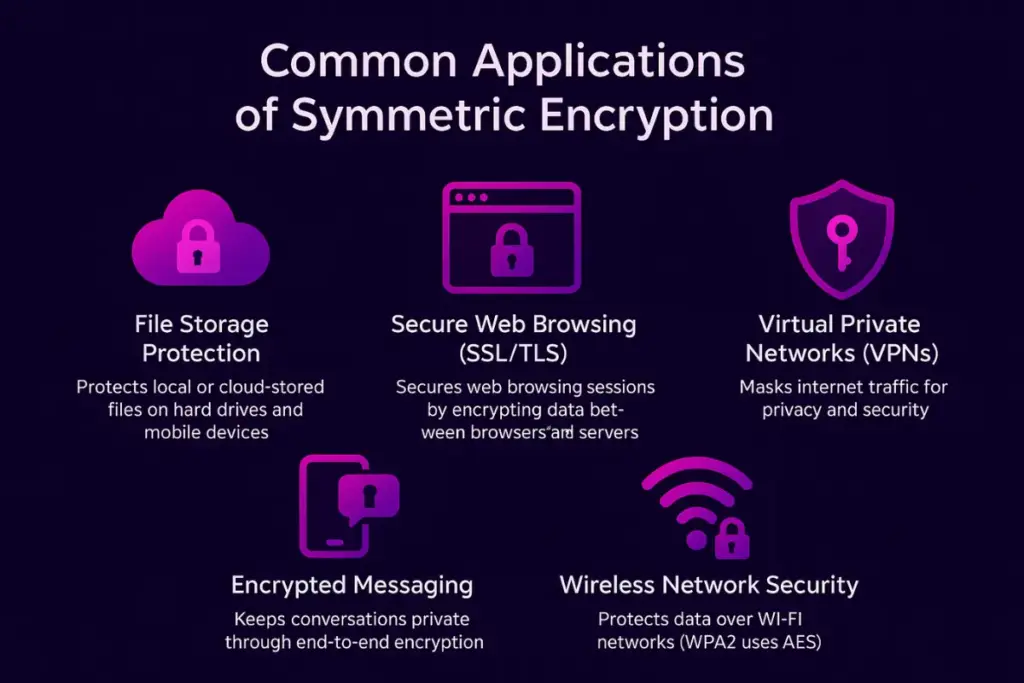
- File Storage Protection
From confidential business documents to personal files, symmetric encryption algorithms safeguards data stored locally, on external drives, and in the cloud. Even if the device is stolen or hacked, encrypted files remain unreadable without the correct key.
- Secure Web Browsing (SSL/TLS)
When you visit a secure website, SSL/TLS uses symmetric encryption after the handshake to protect every byte of information exchanged between your browser and the server. This prevents attackers from intercepting passwords, payment details, or other private data.
- Virtual Private Networks (VPNs)
VPNs use symmetric encryption algorithm to create a secure tunnel for internet traffic. This not only hides browsing activity and masks your IP address but also shields sensitive data when connected to public Wi-Fi or untrusted networks.
- Encrypted Messaging
Modern messaging apps integrate symmetric encryption algorithm into their end-to-end encryption frameworks, ensuring that messages, voice notes, and media files can only be decrypted by the intended recipients—making conversations truly private.
- Wireless Network Security
Wi-Fi protocols such as WPA2 employ symmetric encryption algorithm like AES to protect data sent over wireless networks. This keeps hackers from eavesdropping on communications or gaining unauthorized access to connected devices.
The speed and efficiency of symmetric algorithms make them ideal for encrypting large volumes of data.
Common Types of Symmetric Encryption Algorithm
Symmetric encryption algorithm generally fall into two main categories, based on how they process data: block ciphers and stream ciphers.
Block Ciphers
Block ciphers work by dividing the input data into fixed-size chunks, called blocks (for example, 64-bit or 128-bit blocks). Each block is then encrypted separately, often using a specific mode of operation to make the process more secure.
Popular block cipher algorithms include:
-
DES (Data Encryption Standard) – Once the go-to encryption standard for many industries, DES uses a 56-bit key. While it was considered secure in the 1970s and 80s, advances in computing power have made it vulnerable to brute-force attacks. Learn more about DES encryption.
-
3DES (Triple DES) – Improves on DES by running the algorithm three times with different keys, greatly increasing security. However, it’s slower and is gradually being phased out in favor of more modern algorithms. Discover the Triple DES algorithm.
-
AES (Advanced Encryption Standard) – The current industry standard and widely used worldwide. AES supports key sizes of 128, 192, or 256 bits, offering strong security while maintaining excellent performance. Explore AES details and examples.
-
Blowfish – Known for its speed and flexibility, Blowfish allows variable key lengths (up to 448 bits). It is fast and still used in certain applications, but it has mostly been replaced by newer ciphers. Read how Blowfish encryption works.
-
Twofish – The successor to Blowfish, Twofish offers better security and performance. It supports key sizes up to 256 bits and remains a solid choice for secure applications. Learn more about Twofish encryption.
Stream Ciphers
Stream ciphers handle data one bit or byte at a time, rather than in blocks. This makes them especially useful for real-time data such as audio or video streaming, where speed and continuous encryption are essential.
Common examples include:
-
RC4 – Extremely fast and once widely used in protocols like WEP and TLS. However, it has significant weaknesses and is now considered insecure.
-
Salsa20/ChaCha20 – Modern stream ciphers that are both secure and efficient. ChaCha20, in particular, is used by Google in TLS (Transport Layer Security) for encrypting HTTPS connections, offering both speed and strong protection.
Strengths of Symmetric Encryption Algorithm
-
High Performance – Symmetric encryption algorithm is generally much faster than asymmetric encryption algorithm because it uses simpler mathematical operations. This makes it suitable for applications that require real-time or high-speed data processing, such as secure video calls, online gaming, or large file transfers.
-
Low Resource Usage – It consumes fewer processing resources, allowing it to work efficiently even on low-power devices like IoT sensors, smart cards, and embedded systems. This is especially important when memory, CPU power, or battery life is limited.
-
Simplicity – Only one key is required for both encryption and decryption, making the process easier to implement and manage compared to systems that require multiple keys.
-
Efficient for Large Data – Symmetric encryption can encrypt and decrypt large amounts of data without significant performance loss, making it ideal for securing databases, backups, and full disk drives.
Weaknesses and Drawbacks
-
Key Distribution Problem – Securely sharing the secret key with the recipient is a major challenge. If the key is intercepted during transmission, all encrypted data can be exposed.
-
No Non-Repudiation – Since both parties use the same key, it is impossible to prove who encrypted or sent the data. Either party could deny responsibility, and there is no cryptographic way to confirm it.
-
Scalability Issues in Large Networks – The number of keys needed grows rapidly as more participants are added. For example, a network of 100 users would require 4,950 unique keys for secure communication between all pairs.
-
Vulnerability to Key Compromise – If the shared key is stolen or leaked, the attacker can immediately read all past and future encrypted messages and also create messages that appear authentic.
Symmetric vs. Asymmetric Encryption
Symmetric and asymmetric encryption are two fundamental approaches to securing data, and they differ significantly in how they handle keys and operate.
-
Symmetric encryption uses a single secret key shared by both the sender and receiver. It is fast and efficient, making it ideal for encrypting large amounts of data quickly. However, securely sharing this secret key between parties can be challenging.
-
Asymmetric encryption uses a pair of keys—a public key that can be shared openly and a private key kept secret. While slower and more computationally intensive, it solves the key distribution problem and supports digital signatures, which help verify authenticity and ensure data integrity.
In many secure communication systems, these two methods are combined: asymmetric encryption securely exchanges the symmetric key, which is then used to encrypt the bulk of the data efficiently.
For a detailed comparison of symmetric and asymmetric encryption—including their strengths, weaknesses, and use cases—please see our dedicated article: Symmetric vs Asymmetric Encryption.
Choosing the Right Symmetric Encryption Algorithm
Selecting the best symmetric encryption algorithm depends on your specific needs and the environment in which it will be used. Here are some key factors to consider:
-
Security Strength:
Choose an algorithm that provides strong protection. For highly sensitive information, AES with 256-bit keys (AES-256) is widely recommended because it resists all known practical attacks. Using weaker algorithms or shorter keys can leave data vulnerable. -
Performance:
Different algorithms perform better on different devices. For instance, ChaCha20 is optimized for mobile and embedded devices where processing power and battery life are limited. It offers strong security while being fast and lightweight. -
Compatibility:
Ensure that the algorithm is supported across all platforms and systems you intend to use. Older devices or software might not support newer encryption standards, which can cause issues with data exchange or access. -
Regulatory Compliance:
Some industries or governments require specific algorithms to meet legal standards. For example, the US federal government mandates AES for protecting classified and sensitive data. Make sure to select algorithms that comply with relevant regulations in your sector.
Best Practices for Using Symmetric Encryption Algorithm
-
Enforce complex, random, and unique key creation:
Always generate keys using strong random number generators to avoid predictable or weak keys. Each key should be unique to prevent reuse that could compromise security. -
Use secure channels (like TLS) for key exchange:
Since symmetric encryption algorithm requires sharing the secret key, use secure communication protocols such as TLS (Transport Layer Security) to safely exchange keys without risk of interception. -
Store keys separately from encrypted data:
Keep encryption keys in a secure, isolated location—such as a hardware security module (HSM) or dedicated key management system—to reduce the risk of both keys and data being compromised together. -
Update and rotate keys periodically:
Regularly changing keys limits the damage if a key is leaked or stolen. Key rotation policies should be based on the sensitivity of data and organizational security requirements. -
Combine encryption with integrity checks (MACs):
To ensure data hasn’t been tampered with, pair symmetric encryption algorithm with Message Authentication Codes (MACs) or similar mechanisms that verify data integrity and authenticity.
Future Trends in Symmetric Encryption
As technology advances, especially with the rise of quantum computing, researchers are closely examining how current symmetric encryption algorithms will hold up against new types of cyber threats. While quantum computers could potentially break some forms of encryption in the future, symmetric algorithms like AES with large key sizes (e.g., AES-256) are currently considered robust enough to resist these emerging threats for the foreseeable future.
At the same time, new and more efficient algorithms such as ChaCha20 are gaining popularity. These algorithms offer strong security while performing exceptionally well on low-power and resource-constrained devices like smartphones, IoT gadgets, and embedded systems, making them highly relevant in today’s connected world.
Moreover, the field of cryptography is moving toward more sophisticated hybrid cryptosystems that combine the strengths of symmetric and asymmetric encryption algorithms. These systems aim to improve both scalability and security to meet the demands of increasingly complex and large-scale digital environments — such as cloud computing, large IoT networks, and secure communications across distributed systems.
As the landscape evolves, ongoing research and development will continue to refine symmetric encryption techniques to ensure they remain a foundational pillar of data security well into the future.
Summary
Symmetric encryption algorithms continue to be a cornerstone of modern data security, offering fast and efficient protection by using a single, shared secret key for both encrypting and decrypting information. Their speed and simplicity make them ideal for securing large volumes of data in applications ranging from private communications to encrypted storage solutions.
While key management—including secure key distribution and storage—remains a critical challenge, the benefits of symmetric encryption far outweigh these difficulties. As a result, it remains an indispensable tool in the cybersecurity toolkit.
Understanding how symmetric encryption algorithm works, their strengths and limitations, and best practices for its use is essential knowledge for anyone working in IT, cybersecurity, networking, or any field that involves protecting sensitive digital information.
Further Reading
- National Institute of Standards and Technology (NIST): Symmetric-Key Algorithms
- OWASP: Cryptographic Storage Cheat Sheet
- RFC 4880 (OpenPGP Standard)
- Cryptography Stack Exchange
- IBM Developer: Introduction to Symmetric Encryption
These resources offer a mix of official standards, practical guidelines, and educational material to help you master symmetric encryption and its applications.