The Triple Data Encryption Standard (3DES) is a cornerstone in the world of secure digital communications. As businesses and individuals increasingly rely on data-driven processes, understanding symmetric encryption algorithms like this is crucial for ensuring data confidentiality and resisting evolving cybersecurity threats.
What is the Triple Data Encryption Standard
The triple data encryption standard is an advanced cryptographic algorithm built on the foundations of the original data encryption standard (DES). In simple terms, it enhances security by applying the DES cipher—one of the earliest and most trusted block ciphers—three separate times to each data block. This process significantly increases resistance to common attack methods, making it the preferred choice for industries requiring robust security measures.
A Brief History of Triple DES
Triple Data Encryption Standard was introduced in the late 1990s as a response to the weaknesses discovered in the original Data Encryption Standard (DES). DES, which used a 56-bit key, had become vulnerable to brute-force attacks as computing power increased.
To extend DES’s life without completely redesigning encryption systems, NIST approved Triple Data Encryption Standard. Instead of a brand-new algorithm, Triple DES applies the DES cipher three times in succession, which increases the effective key length to 112- or 168-bits.
This approach allowed industries such as banking and payment processing to maintain backward compatibility with DES while gaining stronger security. For more than a decade, 3DES was a trusted workhorse for protecting sensitive data worldwide.
How Does the Triple Data Encryption Standard Algorithm Work?
At its core, triple data encryption standard works by performing a series of encryption and decryption operations on each block of plaintext using multiple keys. The process is often described as Encrypt–Decrypt–Encrypt (EDE), because the data passes through three stages:
-
First Encryption (Key 1):
The plaintext block is first encrypted with the first key. This step begins the transformation of readable data into an unreadable form. -
Decryption (Key 2):
The result of the first step is then decrypted using a second key. At first glance, this may seem counterintuitive—why decrypt in the middle of an encryption process? The reason is compatibility. This middle decryption step allows systems that still use single DES to remain compatible with 3DES in a “two-key” setup. -
Second Encryption (Key 3):
Finally, the data is encrypted again with a third key. This last step ensures that the output is securely scrambled into ciphertext.
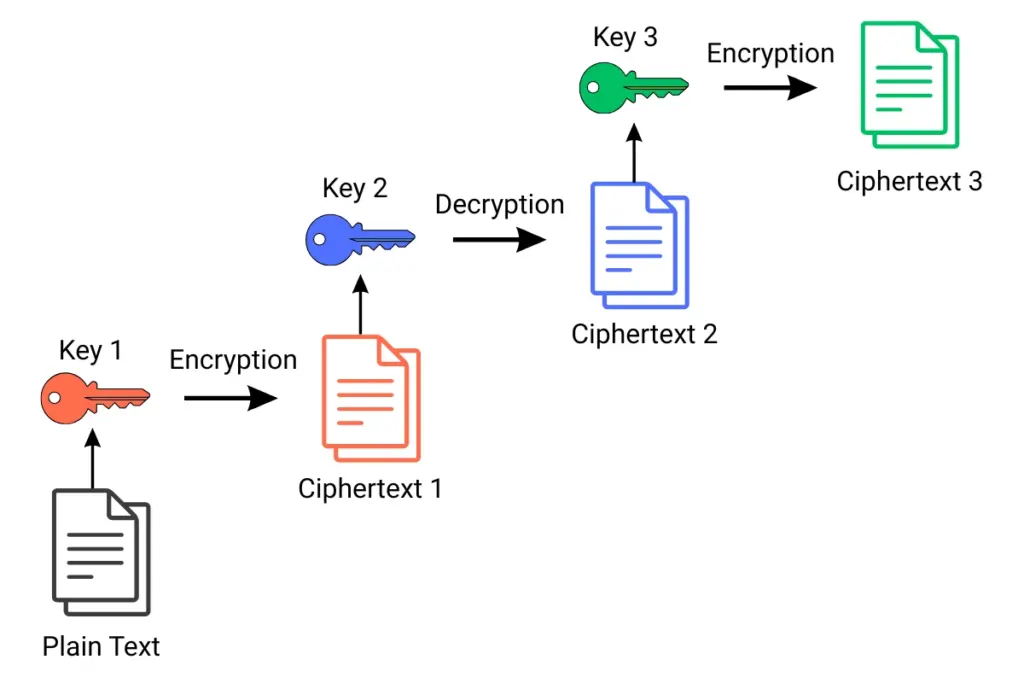
The outcome of this three-step cycle is a ciphertext that is far stronger than what single DES could achieve. By layering encryption in this way, triple data encryption standard makes it exponentially harder for attackers to guess the keys, even if they attempt brute-force methods.
Keying Options in 3DES
There are two widely used variants of Triple DES, based on how many independent keys are employed:
-
Two-Key 3DES (2TDEA):
Uses two keys (Key 1 and Key 2), while Key 3 is the same as Key 1. This provides 112-bit effective security, which is still vastly stronger than single DES but weaker than the three-key version. -
Three-Key 3DES (3TDEA):
Uses three independent keys, offering 168-bit effective security. This is the most secure form of Triple DES and the one most often used in high-security systems.
Why Use the Triple Data Encryption Standard?
The Triple Data Encryption Standard was created as a way to make the original DES encryption stronger without having to build an entirely new system from scratch. Back when computers became powerful enough to break DES, many organizations were worried about the safety of their sensitive data. Instead of replacing everything, they could simply “upgrade” to 3DES, which worked like DES but added extra layers of security.
Think of it like putting your valuables in a safe. With DES, you lock the safe once. With Triple DES, you lock it three times with different keys, making it much harder for anyone to break in.
This “plug-and-play” upgrade was especially helpful for banks, governments, and businesses that relied heavily on DES but wanted more protection without changing all their systems.
Key Benefits of Triple Data Encryption Standard
-
Stronger Security:
Because the data is locked three times, triple data encryption standard is much harder to crack. This makes it a safe choice against brute-force attacks (where hackers try every possible key until one works). -
Works with Old Systems:
Companies didn’t have to throw away their old systems built on DES. Triple data encryption standard was designed to work with them, so the upgrade was smooth and affordable. -
Trusted and Tested:
Since it was based on DES, which had already been studied for years, 3DES was seen as reliable. Organizations felt confident using it for important tasks like protecting financial transactions. -
Approved for Industry Use:
For many years, international standards and government regulations required triple data encryption standard for secure communication, especially in industries like banking, credit card systems, and defense.
Drawbacks of Triple DES
Even though Triple DES was a big improvement, it wasn’t perfect. Some of its weaknesses include:
-
Slower Performance:
Since it encrypts data three times, 3DES is slower than modern algorithms like AES. This can be a problem when handling large amounts of data. -
Harder to Manage Keys:
Instead of just one key, 3DES uses two or three. Managing these keys securely can be tricky and increases the chance of mistakes.
Triple DES vs. Other Encryption Standards
Encryption has come a long way, and while Triple Data Encryption Standard was once a trusted standard, it eventually had to share the stage with newer algorithms like Blowfish, Twofish, and AES. Each has its own strengths and weaknesses, and the choice often depends on the balance between security, speed, and compatibility.
Triple DES vs. Single DES
Single DES uses a 56-bit key, which might have been secure back in the 1970s, but modern computers can crack it in hours or even minutes with brute force. That’s why DES alone is no longer safe for protecting sensitive information.
Triple DES fixes this weakness by applying the encryption three times with different keys. In its strongest form (the 3-key version), it has an effective key length of 168 bits, which makes it millions of times harder to break than single DES. In short:
-
DES = one lock, easy to pick today.
-
3DES = three locks in a row, much harder to pick.
Triple DES vs. AES
Eventually, even Triple DES started showing its age. That’s where AES (Advanced Encryption Standard) came in. AES quickly became the new global standard for encryption because:
-
It’s faster than Triple DES, especially on modern hardware.
-
It’s more secure, using larger block sizes (128 bits) and key sizes (128, 192, or 256 bits).
-
It’s widely adopted, making it the go-to choice for everything from online banking to securing Wi-Fi.
In comparison, 3DES is slower and less secure, which is why it’s being phased out. Still, you’ll sometimes find it in legacy systems or industries where compliance rules haven’t fully moved on yet.
Triple DES vs. Blowfish and Twofish
-
Blowfish and Twofish are other block ciphers designed to be fast and secure. Blowfish is older and known for being simple and efficient, while Twofish (a finalist in the AES competition) was built to handle very large keys and still perform well.
-
Unlike 3DES, these algorithms were not limited by the structure of DES. However, they didn’t gain the same universal acceptance as AES, so their use today is more niche.
Performance and Efficiency Considerations
While triple data encryption standard strengthened security, it came with a trade-off: performance.
-
Triple Computation: Since the DES operation runs three times per encryption/decryption cycle, it’s significantly slower than modern ciphers like AES.
-
Impact on High-Volume Systems: In applications that process thousands of transactions per second (e.g., banking networks), the overhead can cause delays and higher resource usage.
-
AES Advantage: AES was designed to be both secure and efficient, especially on modern hardware where AES instructions are optimized at the processor level.
In short, triple data encryption standard is reliable for legacy compatibility but not practical for performance-sensitive applications today.
Applications of the Triple Data Encryption Standard
For many years, the Triple Data Encryption Standard (3DES) was one of the most trusted tools for protecting sensitive information. Because it still worked with older systems, it became a popular choice in industries where security and reliability were non-negotiable.
Here are some of the most common applications of Triple DES:
1. Automated Teller Machines (ATMs)
Every time you insert your card into an ATM, encryption is working in the background to keep your card number and PIN safe. Banks around the world adopted triple data encryption standard to ensure that customer data couldn’t be stolen during ATM transactions.
2. Financial Transfers
From wire transfers to credit card payments, money has to move securely between banks and payment processors. Triple data encryption standard was widely used in these systems to protect the confidentiality and integrity of financial transactions, making sure hackers couldn’t tamper with or intercept payment information.
3. Secure Email and Government Communications
Government agencies and defense contractors often deal with highly sensitive information. Triple data encryption standard was used to secure email, files, and communication lines so that only authorized parties could read the data.
4. Legacy Systems and Critical Infrastructure
Because the triple data encryption standard was designed to work well with systems originally built for DES, many older or specialized systems continued using it long after newer algorithms like AES became available. In areas like telecommunications, utilities, and industrial control systems, 3DES helped extend the security life of critical infrastructure.
Why These Applications Chose Triple Data Encryption Standard
-
Proven Security: At the time, 3DES provided a strong defense against brute-force attacks.
-
Compatibility: It fit easily into systems that had already been using DES.
-
Regulatory Approval: Industries like banking were required by standards bodies to use 3DES for many years.
Even though today AES has taken over as the preferred encryption standard, Triple DES played a crucial role in protecting global financial systems and sensitive communications for decades.
How to Implement the Triple Data Encryption Standard Safely
While Triple DES can still be useful in certain environments, it must be implemented with care. Poor setup or weak management practices can reduce its effectiveness. Here are some best practices:
-
Robust Key Management
Keys are the heart of encryption. If they are weak or exposed, even the strongest algorithm won’t protect your data. Always generate keys using secure, random methods rather than predictable patterns. For maximum safety, store these keys in Hardware Security Modules (HSMs), which are devices designed specifically to keep cryptographic keys safe from theft or misuse. -
Keep Legacy Software Updated
Many systems still rely on older software that was originally designed for DES. If you’re using Triple DES with such systems, make sure everything is updated and patched. This ensures that vulnerabilities are fixed and that your system remains compatible with stronger encryption practices. If updates aren’t possible, start planning for a migration to modern algorithms like AES. -
Monitor for Vulnerabilities
Cybersecurity threats evolve constantly. What is secure today may not be tomorrow. Stay on top of security advisories and industry best practices, and review your encryption setup regularly. Continuous monitoring allows you to react quickly if new weaknesses in Triple DES are discovered. -
Ensure Policy Compliance
Many industries, especially finance and government, have strict security regulations. Conduct regular audits and compliance checks to make sure your use of Triple DES aligns with these standards. Failing to comply could lead to penalties, even if your encryption is technically strong.
Potential Risks and How to Mitigate Them
Even though Triple DES is very secure, it’s not invincible. If used carelessly, it can leave systems exposed. Here are some common risks and how to reduce them:
-
Weak Key Choices
The security of Triple DES depends heavily on the quality of the keys. If the same key is reused across all three encryption steps, the algorithm doesn’t add much strength—it’s almost like using single DES again. To avoid this, always use different, randomly generated keys for each stage of encryption. -
Side-Channel Attacks
Attackers don’t always go after the math behind encryption—they often target the way it’s implemented. For example, they can measure how long a system takes to perform operations or monitor its power usage to guess the keys. These are called side-channel attacks. The best defense is to rely on hardware and software that have been tested and certified against such threats. -
Deprecation Concerns
Technology keeps moving forward, and many industries are phasing out Triple DES in favor of stronger algorithms like AES. While Triple DES may still be supported, it’s not the future of encryption. To stay ahead, organizations should plan a gradual migration to AES or other modern standards to ensure long-term security.
Recent Developments and the Future of Triple DES
In recent years, triple data encryption standard has slowly been stepping aside to make room for newer and stronger encryption methods. Global security standards are phasing it out because, while still secure in some cases, it’s no longer considered the best option.
For example, the Payment Card Industry Data Security Standard (PCI DSS)—which sets the rules for handling credit and debit card data—has already set deadlines for when Triple DES can no longer be used in new systems.
That said, not every organization can drop it overnight. Some older systems, especially in banking and government, are so deeply built around Triple DES that they still rely on it. In those cases, support continues until a safe and practical migration to modern algorithms, like AES, can be made.
Regulatory and Compliance Relevance
Even though NIST has deprecated triple data encryption standard, it continues to appear in compliance standards, especially in payment systems.
-
PCI DSS (Payment Card Industry Data Security Standard): Until recently, 3DES was allowed for encrypting cardholder data, but new updates set a clear phase-out timeline.
-
Government & Industry Guidance: NIST SP 800-131A has formally disallowed 3DES for most new applications after 2023.
-
Legacy Exceptions: Some industries still allow 3DES in older systems where replacing hardware/software is not yet feasible.
For organizations, the key compliance takeaway is: if you’re still using 3DES, you should already have a migration plan to AES. Regulators won’t accept 3DES as a long-term solution.
Optimal Use Cases Today
Although most organizations are moving toward AES and other modern encryption standards, there are still some situations where Triple Data Encryption Standard continues to be useful. Its value today is mostly tied to systems that can’t yet upgrade due to cost, complexity, or compatibility issues.
Here are the main scenarios where Triple DES is still relevant:
-
Data-at-Rest Security
In some older hardware or embedded systems, upgrading to AES isn’t possible because of processing limitations. In these cases, Triple DES can still be used to protect stored data until a hardware refresh is possible. -
Secure Enclaves in Legacy Environments
Many industries, such as finance and government, still run critical legacy systems that rely on Triple DES. In these environments, it provides a layer of protection while organizations plan and implement a full migration to stronger algorithms. -
Interoperability Across Networks
Not every organization or partner has migrated away from Triple DES. When global networks, payment processors, or partners are still using it, maintaining support ensures compatibility and smooth communication between systems.
Conclusion: Balancing Security and Performance
Triple DES still plays an important role in protecting sensitive data, especially in industries that depend on older systems. Its three layers of encryption make it much stronger than the original DES, offering reliable protection against most attacks.
For organizations running legacy systems, Triple DES can serve as a practical short-term solution that keeps data secure and helps meet compliance requirements.
That said, it’s not the future of encryption. For new projects and modern systems, stronger and more efficient algorithms like AES are the better choice.
In short: Triple Data Encryption Standard is best seen as a bridge — secure enough for now in the right situations, but not the long-term answer for data protection.
Further Reading



