Triple Data Encryption Standard: Comprehensive Guide & Benefits Explained
Triple Data Encryption Standard: The Ultimate Guide & Benefits Uncovered
The triple data encryption standard is a cornerstone in the world of secure digital communications. As businesses and individuals increasingly rely on data-driven processes, understanding symmetric encryption algorithms like this is crucial for ensuring data confidentiality and resisting evolving cybersecurity threats.
Understanding the Triple Data Encryption Standard
The triple data encryption standard is an advanced cryptographic algorithm built on the foundations of the original data encryption standard (DES). In simple terms, it enhances security by applying the DES cipher—one of the earliest and most trusted block ciphers—three separate times to each data block. This process significantly increases resistance to common attack methods, making it the preferred choice for industries requiring robust security measures.
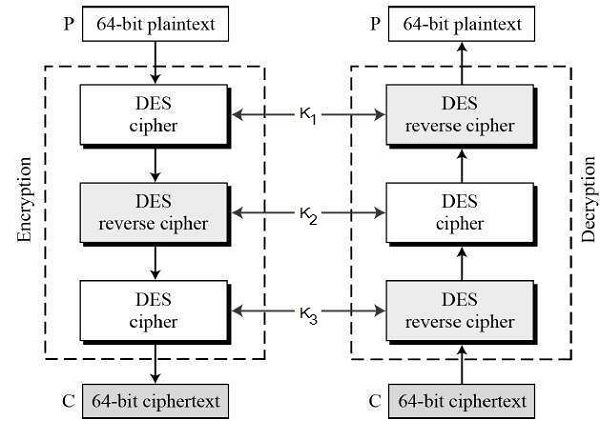
How Does the Triple Data Encryption Standard Algorithm Work?
The triple data encryption standard algorithm operates by sequentially encrypting, decrypting, and re-encrypting each data block using either two or three unique keys. Each cycle consists of the following steps:
- First Encryption: The data block is encrypted using a DES key (Key 1).
- Decryption: The output is decrypted using a second DES key (Key 2).
- Second Encryption: The result is encrypted again with a third DES key (Key 3).
In practice, variants like 2-key and 3-key triple DES exist, with the most secure using all three keys independently. This process achieves a much higher level of security compared to single DES by exponentially increasing the exhaustion required for brute-force attacks.
Why Use the Triple Data Encryption Standard?
The primary motivation for using the triple data encryption standard is its ability to boost cryptographic strength without redesigning an entirely new system. With threats constantly shifting, this plug-and-play upgrade ensures that organizations leveraging legacy systems can enhance data protection while maintaining system compatibility.
Key Advantages
- Enhanced Security: Triple DES is far more resilient against brute-force and cryptanalytic attacks than its predecessor.
- Backward Compatibility: Organizations with systems built around classic DES can easily transition to triple DES with minimal modifications.
- Proven Algorithmic Integrity: Built on extensively evaluated algorithms, it provides predictable and reliable protection.
- Regulatory Approval: Triple DES meets many international security standards, often making it a requirement in regulated sectors like finance and government.
Limitations
Although the triple data encryption standard strengthens data protection, it does come with certain drawbacks, including:
- Performance: It is slower compared to modern block ciphers due to the three rounds of processing.
- Key Management Complexity: Managing multiple keys increases administrative overhead and the potential for human error.
- Eventual Deprecation: As attack capabilities grow, organizations should prepare for migration to newer algorithms, such as AES.
Triple DES vs. Other Encryption Standards
While block ciphers such as Blowfish and Twofish provide viable alternatives in some contexts, their adoption depends on specific requirements and ecosystem support.
Triple DES vs. Single DES
Single DES employs a 56-bit key, which is now considered inadequate for secure communication. Triple DES ramps up this protection, using effective key lengths of up to 168 bits in the 3-key variant, drastically reducing exposure to brute-force attacks.
Triple DES vs. AES
While triple DES was once the industry standard, the advanced encryption standard (AES) now offers higher performance, stronger security, and widespread adoption. However, triple DES remains relevant in specific legacy systems and compliance-driven environments.
Applications of the Triple Data Encryption Standard
Banking and government organizations have long relied on triple DES to protect sensitive information. Key applications include:
- Automated Teller Machines (ATMs): Safeguarding card data and transaction information.
- Financial Transfers: Ensuring the confidentiality and integrity of wire transfers and payment networks.
- Secure Email and Communications: Securing transmissions between government agencies and contractors.
- Legacy Systems: Maintaining security for critical infrastructure built around DES.
How to Implement the Triple Data Encryption Standard Safely
- Robust Key Management: Always use secure, random key generation and store keys in hardware security modules when possible.
- Update Legacy Software: Ensure integrations are patched and compatible with triple DES or plan migration paths where necessary.
- Monitor for Vulnerabilities: Stay informed of security advisories and industry best practices.
- Policy Compliance: Regularly audit systems to ensure adherence to industry regulations.
Potential Risks and How to Mitigate Them
Despite its strengths, the triple data encryption standard can be vulnerable if implemented incorrectly. The most notable risks include:
- Weak Key Choices: Avoid reusing keys across the three encryption steps; such practices reduce the effective key length and security benefits.
- Side-Channel Attacks: Use hardware and software that are validated and tested against timing and power attacks.
- Deprecation Concerns: Begin migration evaluations to algorithms such as AES to future-proof sensitive systems.
Recent Developments and the Future of Triple DES
Global standards bodies are gradually deprecating triple DES in favor of newer algorithms. For instance, the Payment Card Industry Data Security Standard (PCI DSS) has set timelines for discontinuing its use for new applications. However, certain systems may require ongoing support for triple DES due to their architecture or regulatory environment.
What is Triple Triple Data Encryption Standard?
Some references mention the phrase “triple triple data encryption standard.” While it might sound like an error, it highlights the importance placed on repetitive, layered security. Traditionally, only one layer of 3-pass encryption (encryption, decryption, encryption) is used. Multiple iterations offer diminishing returns but highlight the significance organizations place on redundant protection, especially in ultra-secure settings.
Optimal Use Cases Today
While many organizations are migrating to AES, there remain scenarios where triple DES still provides value:
- Data-at-Rest Security: Where hardware limitations restrict migration.
- Secure Enclaves in Legacy Environments: Ensuring ongoing protection until systems are overhauled.
- Interoperability: Maintaining compatibility with global networks or partners yet to migrate from legacy infrastructure.
Conclusion: Balancing Security and Performance
The triple data encryption standard continues to be vital in securing critical information across various sectors, despite emerging algorithms and rising computational power. Its layered design bestows robust protection, making brute-force and many analytical attacks unfeasible for the vast majority of threats. For organizations seeking an immediate upgrade over DES in legacy systems or requiring compliance with certain standards, triple data encryption standard remains a practical, if transitional, choice.
For organizations developing new systems, consider advanced alternatives like AES. However, for those requiring proven techniques, the security provided by triple DES still secures data when properly implemented and managed.