Triple Data Encryption Standard: Comprehensive Guide & Benefits Explained
Understanding the Foundation
Triple DES emerged as a direct response to the limitations of the original Data Encryption Standard (DES), which became vulnerable to brute-force attacks as computing power increased. The triple data encryption standard algorithm addresses these weaknesses by applying the DES cipher three times to each data block, creating a significantly more secure encryption method.
Developed in the late 1990s, this encryption standard quickly became the backbone of secure communications in banking, e-commerce, and government applications. The algorithm’s strength lies in its ability to take a 64-bit block of plaintext and transform it through multiple encryption rounds, making it exponentially more difficult for unauthorized parties to decrypt.
The process begins with a 168-bit key, though the effective key length is 112 bits due to cryptographic considerations. This key undergoes careful preparation before the actual encryption begins, ensuring maximum security throughout the process.
How the Algorithm Works
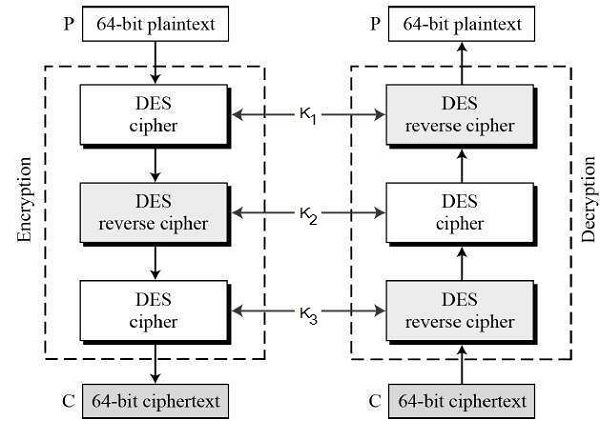
The triple data encryption standard algorithm operates through a sophisticated three-stage process that dramatically increases security compared to single DES encryption. Each stage applies the DES algorithm with different keys, creating layers of protection that would take centuries to break using current technology.
In the first stage, the plaintext undergoes encryption using the first key. The second stage applies decryption using the second key, which might seem counterintuitive but serves a crucial purpose in the algorithm’s design. The final stage encrypts the result using the third key, producing the final ciphertext.
This encrypt-decrypt-encrypt (EDE) approach provides backward compatibility with single DES systems when all three keys are identical. However, maximum security is achieved when using three distinct keys, creating what cryptographers call “three-key Triple DES.”
The algorithm processes data in 64-bit blocks, applying complex mathematical operations that scramble the original information beyond recognition. Each round involves substitution and permutation operations that transform the data through multiple layers of confusion and diffusion.
Key Management Strategies
Effective key management forms the cornerstone of successful Triple DES implementation. Organizations must establish robust procedures for generating, distributing, storing, and retiring encryption keys to maintain security integrity.
Key generation requires high-quality random number generators to ensure unpredictability. Weak keys, which exhibit certain mathematical properties that reduce security, must be avoided through careful validation processes. The system should automatically reject keys that fall into these vulnerable categories.
Distribution of keys presents unique challenges, particularly in distributed systems. Secure key exchange protocols, such as Diffie-Hellman key exchange or public key infrastructure (PKI), help establish shared keys between parties without exposing them to interception.
Storage security demands hardware security modules (HSMs) or secure software vaults that protect keys from unauthorized access. Regular key rotation schedules ensure that even if a key becomes compromised, the exposure window remains limited.
Implementation Across Industries
Financial institutions rely heavily on Triple DES for protecting transaction data, customer information, and inter-bank communications. ATM networks, credit card processing systems, and online banking platforms implement this encryption standard to safeguard billions of dollars in daily transactions.
Healthcare organizations use Triple DES to protect patient records, comply with HIPAA regulations, and secure medical device communications. The algorithm’s proven track record makes it particularly suitable for environments where data integrity and privacy are paramount.
Government agencies implement Triple DES for classified communications, diplomatic cables, and sensitive administrative data. The algorithm’s approval by various national security agencies worldwide demonstrates its reliability for protecting state secrets.
E-commerce platforms integrate Triple DES into their security frameworks to protect customer payment information, personal data, and business communications. The algorithm’s compatibility with existing infrastructure makes it an attractive choice for companies upgrading their security posture.
Performance Considerations
While Triple DES provides excellent security, organizations must consider performance implications when implementing this encryption standard. The algorithm’s three-stage process inherently requires more computational resources than single DES or some modern alternatives.
Processing speed varies significantly based on hardware capabilities, with dedicated cryptographic processors offering substantial performance advantages over software-only implementations. Modern processors with built-in encryption instructions can execute Triple DES operations efficiently, minimizing performance impact.
Memory requirements remain relatively modest, making Triple DES suitable for embedded systems and devices with limited resources. However, the algorithm’s sequential nature can limit parallelization opportunities in high-throughput environments.
Latency considerations become critical in real-time applications. While encryption delays are typically measured in microseconds, they can accumulate in systems processing thousands of transactions per second. Careful system design and hardware selection help minimize these effects.
Security Strengths and Limitations
The primary strength of what is triple data encryption standard lies in its resistance to known cryptographic attacks. The algorithm has withstood decades of analysis by the global cryptographic community, with no practical attacks discovered against properly implemented systems.
Key space expansion represents another significant advantage. While single DES uses a 56-bit key, Triple DES effectively provides 112 bits of security, making brute-force attacks computationally infeasible with current technology.
However, certain limitations must be acknowledged. The algorithm’s age means it lacks some advanced features found in modern encryption standards. Block size remains fixed at 64 bits, which can create security concerns in specific applications processing large amounts of data.
Meet-in-the-middle attacks, while theoretical, represent the most significant known vulnerability. These attacks reduce the effective key length from 168 to 112 bits, though this still provides adequate security for most applications.
Modern Alternatives and Migration
As technology evolves, organizations increasingly consider migration to Advanced Encryption Standard (AES) and other modern algorithms. AES offers superior performance, larger block sizes, and enhanced security features that address Triple DES limitations.
Migration planning requires careful consideration of existing infrastructure, compliance requirements, and security policies. Organizations often implement hybrid approaches, using Triple DES for legacy systems while adopting AES for new implementations.
Timeline considerations vary by industry and regulatory environment. Financial institutions may maintain Triple DES support for years to ensure compatibility with existing ATM networks and payment systems, while other industries might accelerate migration to newer standards.
Cost-benefit analysis helps organizations determine optimal migration strategies. While newer algorithms offer advantages, the proven security and widespread support of Triple DES may justify continued use in certain applications.
Regulatory Compliance
Various regulatory frameworks explicitly reference Triple DES as an acceptable encryption standard. Payment Card Industry Data Security Standard (PCI DSS) continues to recognize Triple DES for protecting cardholder data, though it encourages migration to AES.
Federal Information Processing Standards (FIPS) approval ensures Triple DES meets government security requirements. This certification provides confidence for organizations operating in regulated environments or conducting business with government entities.
International standards organizations maintain Triple DES specifications, ensuring interoperability across global systems. This standardization facilitates secure communications between organizations using different vendors’ implementations.
Compliance audits regularly evaluate Triple DES implementations, checking key management procedures, algorithm configuration, and security controls. Proper documentation and regular testing help organizations maintain compliance status.
Best Practices for Implementation
Successful Triple DES implementation requires adherence to established security practices and careful attention to configuration details. Organizations should develop comprehensive policies covering all aspects of encryption system management.
Regular security assessments identify potential vulnerabilities and ensure continued effectiveness. Penetration testing, code reviews, and cryptographic analysis help maintain security posture as threats evolve.
Training programs ensure staff understand proper encryption procedures, key management responsibilities, and incident response protocols. Security awareness extends beyond IT teams to include all personnel handling encrypted data.
Documentation standards facilitate system maintenance, compliance audits, and knowledge transfer. Detailed records of configuration decisions, key management procedures, and security controls support long-term system sustainability.
Future Outlook
While newer encryption algorithms offer enhanced capabilities, Triple DES maintains relevance in specific applications and industries. Legacy system support, regulatory requirements, and proven security record ensure continued use for years to come.
Quantum computing developments may eventually threaten all current encryption standards, including Triple DES. However, practical quantum computers capable of breaking cryptographic systems remain years away, providing time for orderly migration to quantum-resistant algorithms.
Industry trends favor gradual migration to AES and other modern standards, but Triple DES will likely remain in specialized applications where compatibility and proven security outweigh performance considerations.
The encryption landscape continues evolving, with new threats and technologies driving innovation. Organizations using Triple DES should monitor developments and maintain flexibility to adapt their security strategies as needed.
Triple DES represents a crucial milestone in cryptographic history, providing robust security for countless applications worldwide. Understanding its capabilities, limitations, and proper implementation ensures organizations can leverage this powerful encryption standard effectively while planning for future security needs.